Why forward-looking defense contractors are rethinking their architecture- and choosing a smarter path to CMMC compliance.
The recent breach of Microsoft SharePoint- which compromised highly sensitive data at the National Nuclear Security Administration (NNSA), National Institutes of Health (NIH), and other federal agencies- once again underscores a crucial distinction that PreVeil has consistently highlighted: Compliance is not the same as security.
Microsoft’s GCC High (GCCH) and its associated applications- OneDrive, Outlook, Word, Excel, PowerPoint- store and process data in cloud environments where decrypted content is routinely exposed to the server. These environments may meet compliance requirements, but they do not eliminate the core vulnerability: If a server is breached, the attacker sees what the server sees.
The recent SharePoint attack demonstrates exactly that. Threat actors gained access to data not because it wasn’t encrypted at rest, but because the architecture inherently requires decryption during use. Once inside, attackers were able to access and manipulate sensitive information at will.
A Breach That Shattered Assumptions
This flaw is not unique to SharePoint. It is a systemic vulnerability in the legacy server-centric architectures underlying widely used Microsoft applications. These systems rely on servers that must decrypt data in order to process it- exposing that data to attackers if the server is compromised. This includes government-grade platforms like GCCH. And while GCCH may be the default compliance path for large defense contractors heavily invested in Microsoft infrastructure, its security limitations are not materially different from Microsoft’s commercial offerings. The breach of the NNSA makes that point with uncomfortable clarity.
The Case for End-to-End Encryption
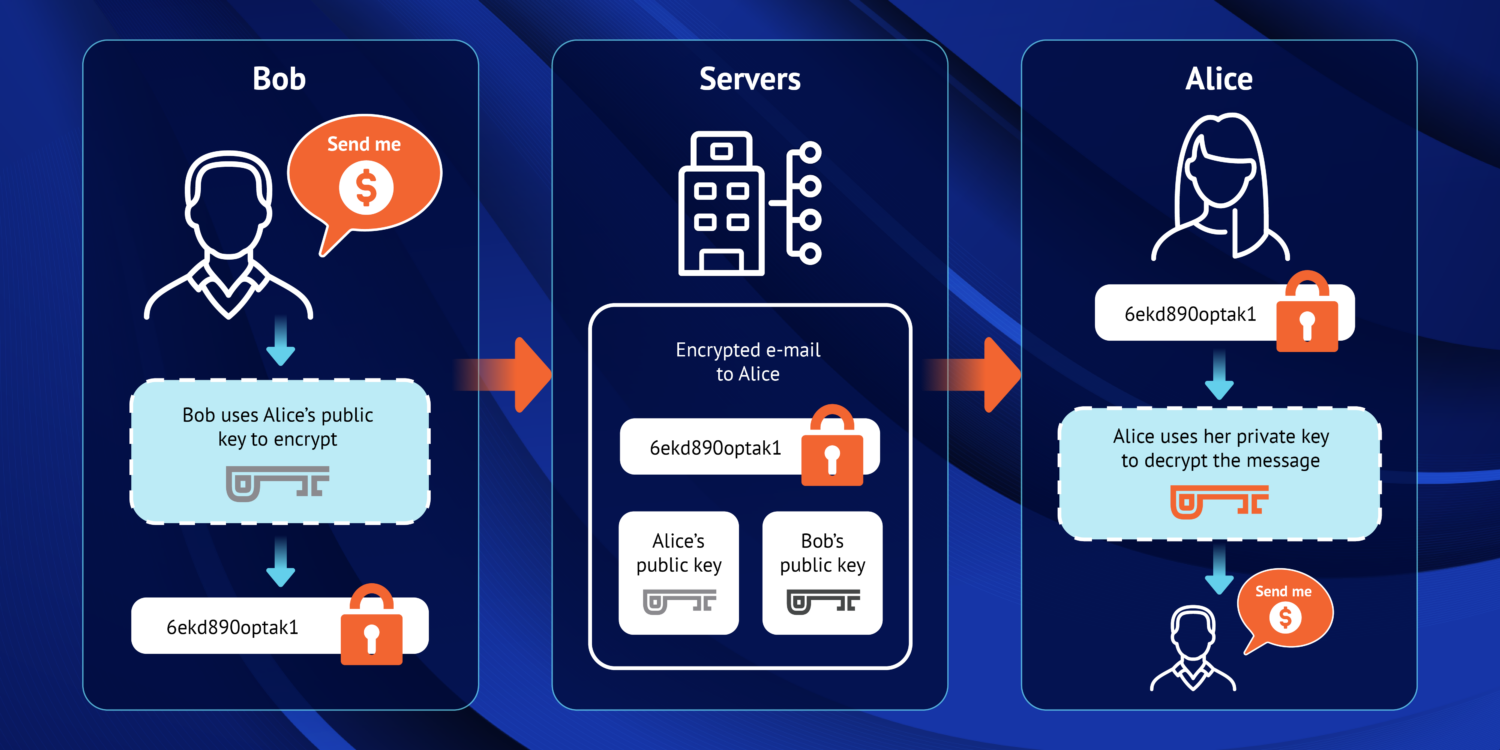
Eliminating this persistent vulnerability requires a fundamental shift in how data is protected—and that shift begins with understanding what end-to-end encryption (E2EE) truly offers. In an E2EE system, data is encrypted on the sender’s device and can only be decrypted by the intended recipient’s device. At no point does the server—whether cloud-based or on-premises—have access to the plaintext data or the keys required to decrypt it. This architecture removes the server entirely from the trust boundary, thereby nullifying the risk of server-side data compromise.
This is not a fringe viewpoint. The National Security Agency (NSA), in its 2021 cybersecurity guidance, explicitly recommended the use of end-to-end encryption to secure collaboration platforms, stating that providers should not have access to the decrypted content or encryption keys. This architectural principle—central to PreVeil’s design—is endorsed as essential to protecting national security systems. Likewise, leading academic cryptographers have long affirmed that only E2EE can reliably protect against threats that exploit centralized infrastructure. The conclusion is widely accepted: If the server can see your data, so can the attacker.
Visit our End-to-End encryption blog for more details on how this technology works:
PreVeil: A Smarter Path to Compliance—and Security
The ongoing push toward CMMC compliance offers organizations in the Defense Industrial Base (DIB) a rare opportunity—not just to meet regulatory requirements, but to fundamentally improve their security posture. While it may be tempting to view CMMC certification as a box-checking exercise, this mindset overlooks a critical business reality: breaches are extraordinarily costly to remediate. Investing in stronger security is not just prudent—it’s smart business.
For larger defense contractors deeply integrated into Microsoft’s ecosystem, GCC High may be the practical path to compliance. But many others—particularly Small and Medium Businesses (SMBs), international organizations, and divisions of larger enterprises involved in defense work—have the flexibility to choose more secure alternatives. PreVeil is one such platform, purpose-built with true end-to-end encryption to protect Controlled Unclassified Information (CUI) while meeting CMMC requirements.
In PreVeil’s architecture, encryption is not just a box checked—it is the core security model. CUI is encrypted before it leaves the user’s device and can only be decrypted by the intended recipient. Keys are never stored on any server, eliminating the very attack vector that compromised SharePoint and other platforms. Even in the event of a server breach, the attacker gains nothing of value.
PreVeil allows organizations to continue using Outlook with full end-to-end encryption, storing encrypted data on PreVeil’s servers rather than Microsoft’s cloud. This maintains familiar workflows while eliminating the server-side vulnerabilities that enabled the SharePoint breach.
Thousands of organizations across the DIB are choosing PreVeil because it makes business sense. Compared to GCC High, PreVeil offers a radically lower cost of compliance, faster and simpler deployment, and proven results—more than 75 customers have achieved perfect 110/110 scores on their CMMC assessments. These are not paper wins; they are evidence that strong security and full compliance can coexist when the right architecture is in place. Yet perhaps the most overlooked benefit is also the most critical: a true upgrade in security. With PreVeil’s end-to-end encryption, organizations aren’t just meeting standards—they’re proactively closing the door on the most common and costly form of data compromise. For those tasked with protecting CUI, choosing better security shouldn’t require a trade-off. With PreVeil, it doesn’t.
Here’s a detailed comparison of how PreVeil compares with GCC High:
| Feature | Microsoft GCC High | PreVeil |
| Best For | Large enterprises with dedicated IT & compliance teams | Organizations of all sizes, particularly SMBs seeking simplicity and affordability |
| Deployment | Requires disruptive and costly migrations of IT systems | Seamlessly integrates with your existing IT setup |
| Cost | High, with significant license fees and documentation challenges | Affordable, with prefilled compliance documentation included, saving tens of thousands |
| Security | Vulnerable, with decrypted content routinely exposed to the server | Unrivaled, with end-to-end encryption ensuring that even in the event of a server breach, attackers see nothing |
| Supplier Collaboration | Requires expensive Guest Licenses for external users | Free, encrypted accounts for external collaborators |
| Ease of Use | Complex, requiring dedicated IT resources to manage & configure | Easy to deploy and manage, even for SMBs with limited IT staff |
E2EE Is Becoming the Standard
Compliance frameworks are increasingly recognizing the need to align with real security—not just checkbox requirements. A clear example of this shift is the ITAR 120.54 encryption carveout, developed by the NSA and the State Department. It formally validates properly implemented end-to-end encryption (E2EE) as a secure and compliant method for transmitting export-controlled data over the internet. This carveout affirms what security professionals have long argued: E2EE is not only best practice—it is essential to protecting sensitive national defense information in today’s threat landscape.
The Bottom Line: Aligning Compliance with Security
The SharePoint breach at NNSA makes one thing unmistakably clear: even systems designed for government use remain vulnerable when their architectures expose decrypted data to the server. For organizations across the Defense Industrial Base, CMMC is more than a compliance mandate—it is a moment of strategic choice.
That choice is whether to continue investing in architectures that merely meet regulatory minimums or to adopt systems that fundamentally eliminate exposure. End-to-end encryption delivers on that promise by ensuring that sensitive data is never visible to the server and therefore never accessible to an attacker, even if the infrastructure is compromised.
CMMC should be seen as a catalyst to adopt security models that provide both provable compliance and lasting resilience. For organizations safeguarding national defense information, now is the time to align compliance obligations with uncompromising security.