Encrypted Email + File Sharing for Defense and Regulated Industries
Proven CMMC, NIST, ITAR, and HIPAA compliance made simple and affordable

Military Grade Email + File Sharing Trusted Worldwide
100,000
Users
20,000
Organizations
2,500
Defense Contractors
75+
Achieved CMMC
Platform
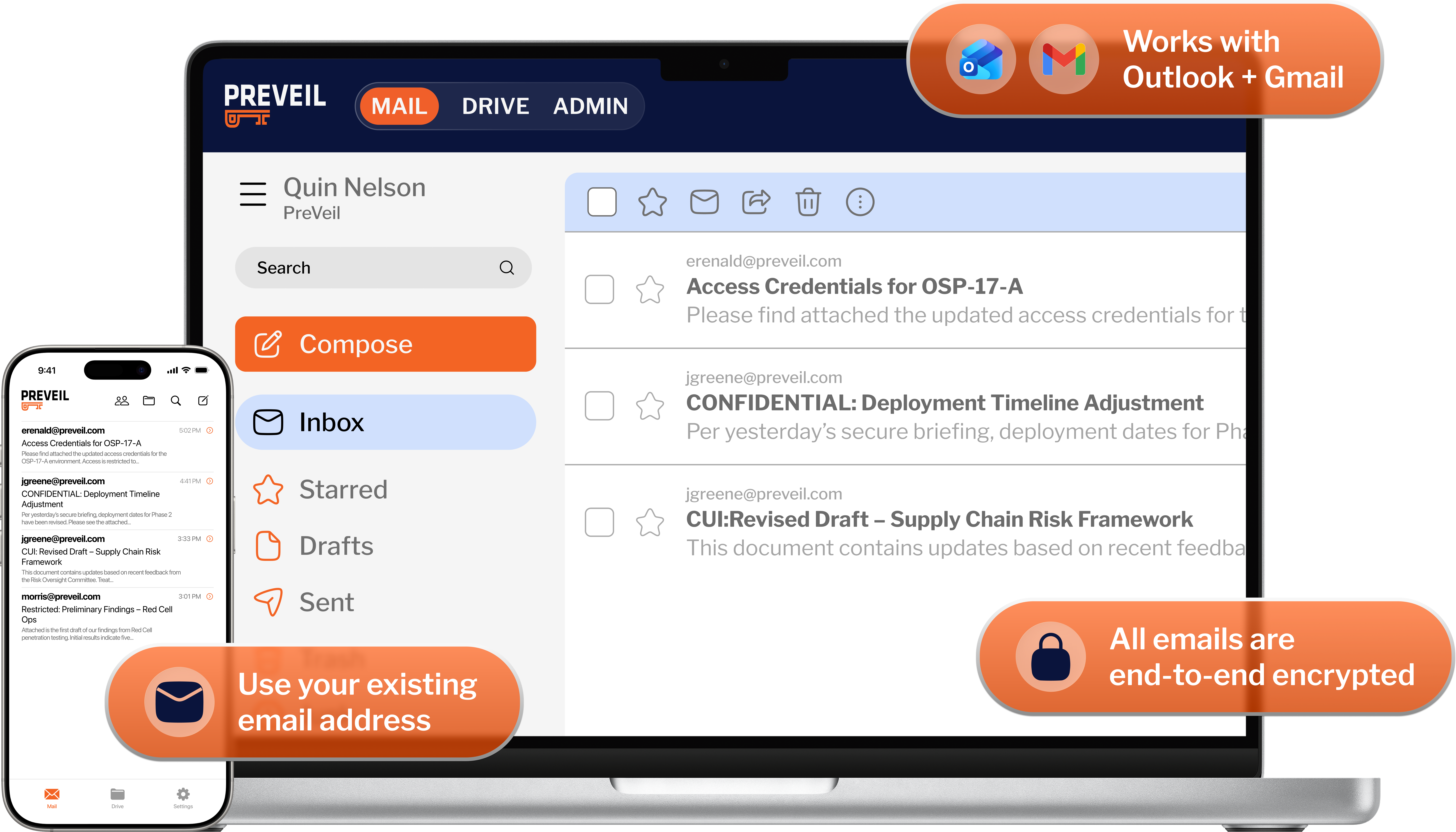
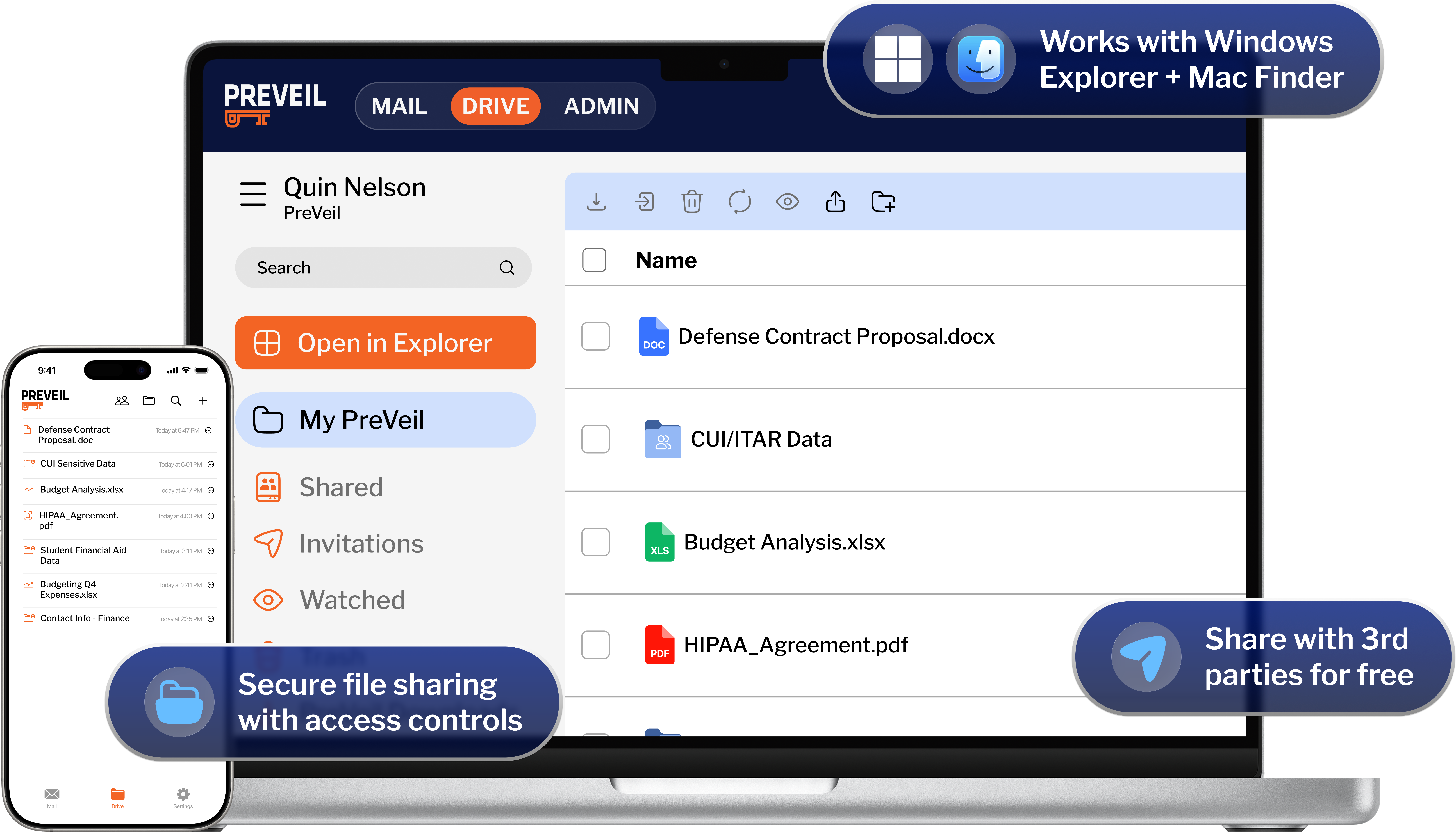
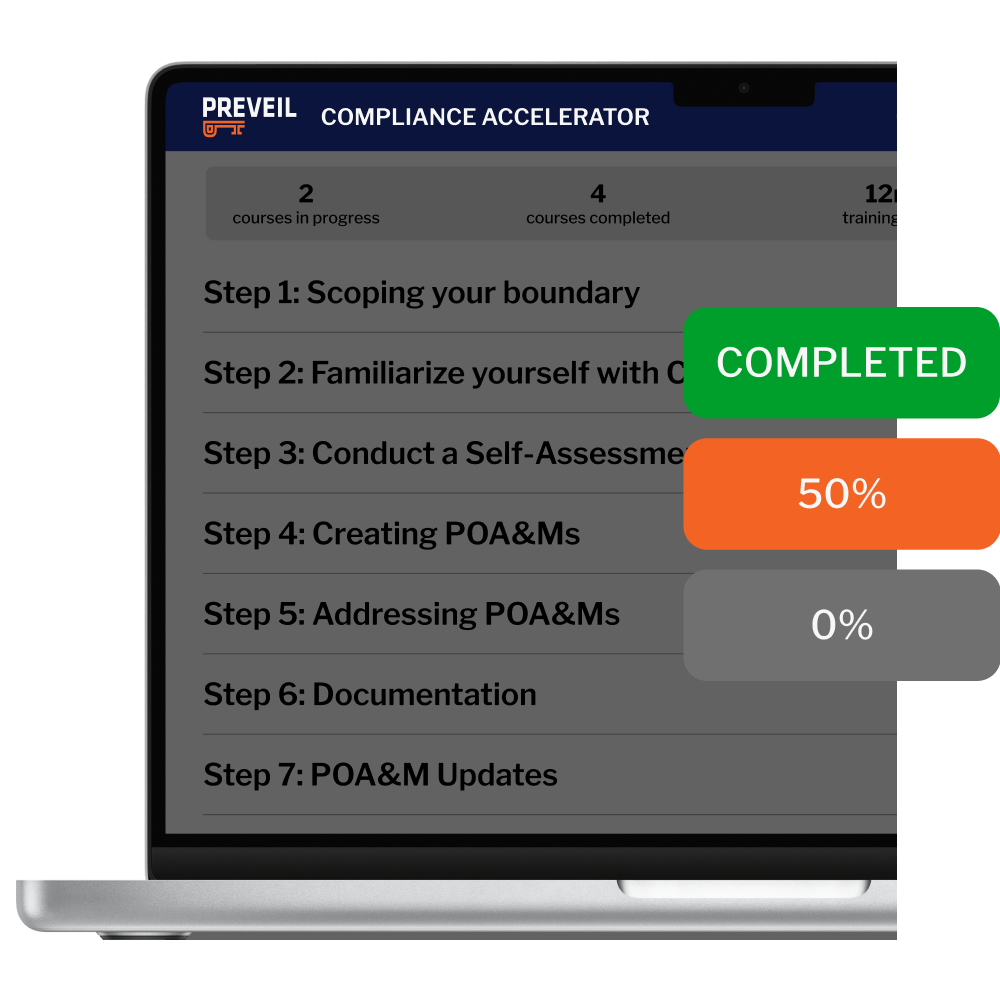
For a locked-down enclave or the whole organization, PreVeil Email, Drive, and Compliance Accelerator secure your files and simplify compliance.

5 Years in a Row
PC Mag: Best Encrypted Email & File Sharing
“With PreVeil, you get…end-to-end encrypted secure cloud storage along with secure email that’s tough enough for business but extremely easy to use, all while keeping your existing email address.”
– Neil Rubenking, PC Magazine
Proven Compliance in the Most Demanding Environments
PreVeil meets the toughest standards of CMMC and ITAR—proven by the customers below who achieved perfect 110/110 CMMC scores

Defense Contractor
“We got the GCC High quote and it was just crazy: It was over $200,000 for 33 users…the PreVeil quote was 1/10th of that and checked every box“
That same level of security enables compliance with HIPAA, GLBA, CJIS, and more.

Save 77% on CMMC
PreVeil Pass is built for Small to Medium sized contractors. It includes 3 licenses, assessment-ready CMMC documentation, 1:1 support, and access to our partner network—all starting at $450/month.
Unrivaled Security to Meet Compliance
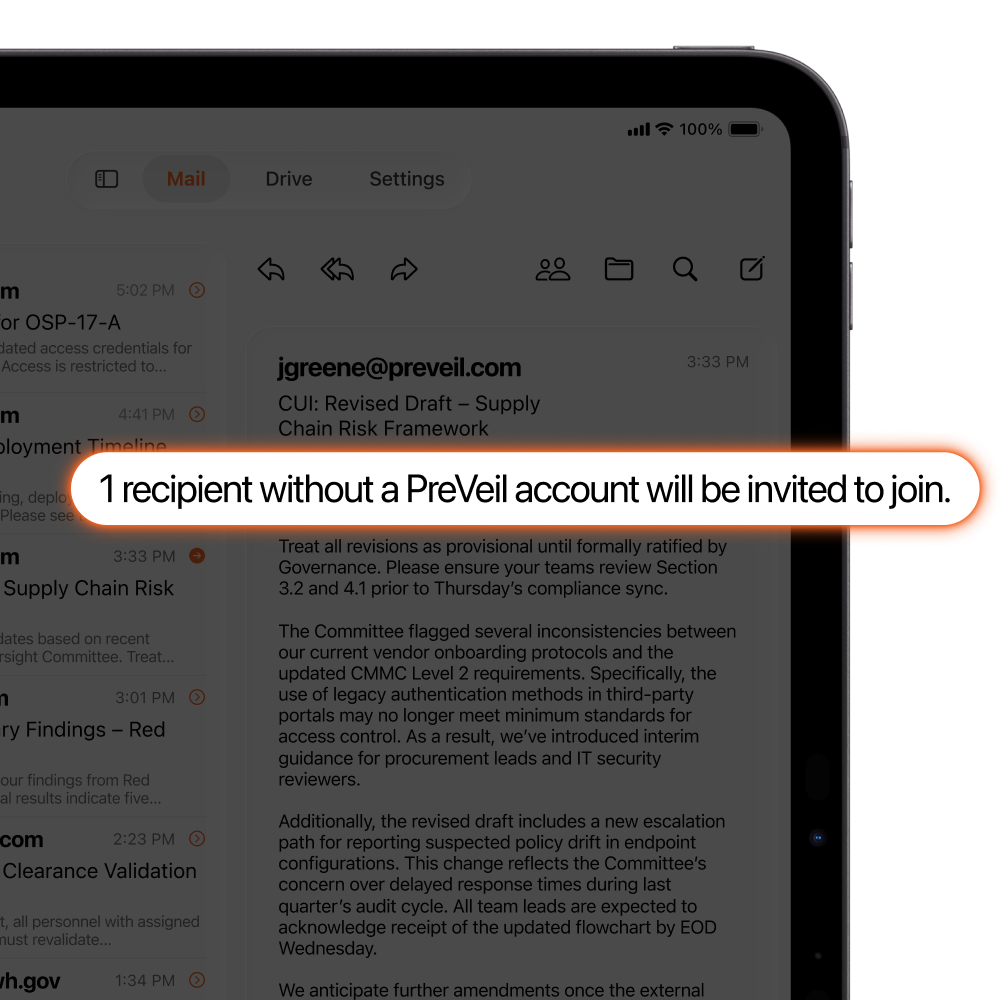
End-to-End Encryption
Data is encrypted from the sender’s device to the recipient, blocking hackers even if servers are breached.
Zero Trust Architecture
Protects against insider and admin threats, plus built-in ransomware protection ensures quick recovery.
Ultra Private
Nobody but the intended recipient – not even PreVeil – can read users’ messages and files
Industry-Leading Events
Ready to get started with PreVeil?
PROUDLY MADE IN THE USA
PreVeil is 100% Designed & Developed in the USA