12 Steps to Get your Organization Ready for CMMC
If you are a defense contractor, you will need to meet Cybersecurity Maturity Model Certification (CMMC) requirements to continue working for the DoD. CMMC is now final. It became effective on Dec 16, 2024 and enters into contracts mid-2025.
We created the following CMMC Compliance Checklist to help you expedite your compliance, lower your costs, & maintain your competitive position in the DIB.
What is CMMC?
CMMC is designed to raise cybersecurity levels throughout the DIB by better protecting FCI CUI. Importantly, CMMC doesn’t change existing cybersecurity requirements— it just steps up enforcement. Under CMMC, the vast majority of defense contractors will need to pass independent third-party assessments.
- Level 1 is for organizations working with FCI only and requires compliance with FAR 52.204-21.
- Level 2 is for organizations working with CUI and requires compliance with the 110 security controls specified in NIST 800-171. The vast majority of organizations (95%) will be required to undergo third-party assessments conducted by CMMC Third Party Assessor Organizations (C3PAOs).
- Level 3 is for organizations working with CUI and subject to Advanced Persistent Threats (APTs) and requires compliance with NIST 800-172, with assessments conducted by the DoD’s DIBCAC.
Now that you know what CMMC compliance is, you’ll want to check out the timeline of its rollout to make sure you are on track to achieve it.
CMMC Timeline
CMMC is now final and will start appearing in DoD contracts in mid-2025:
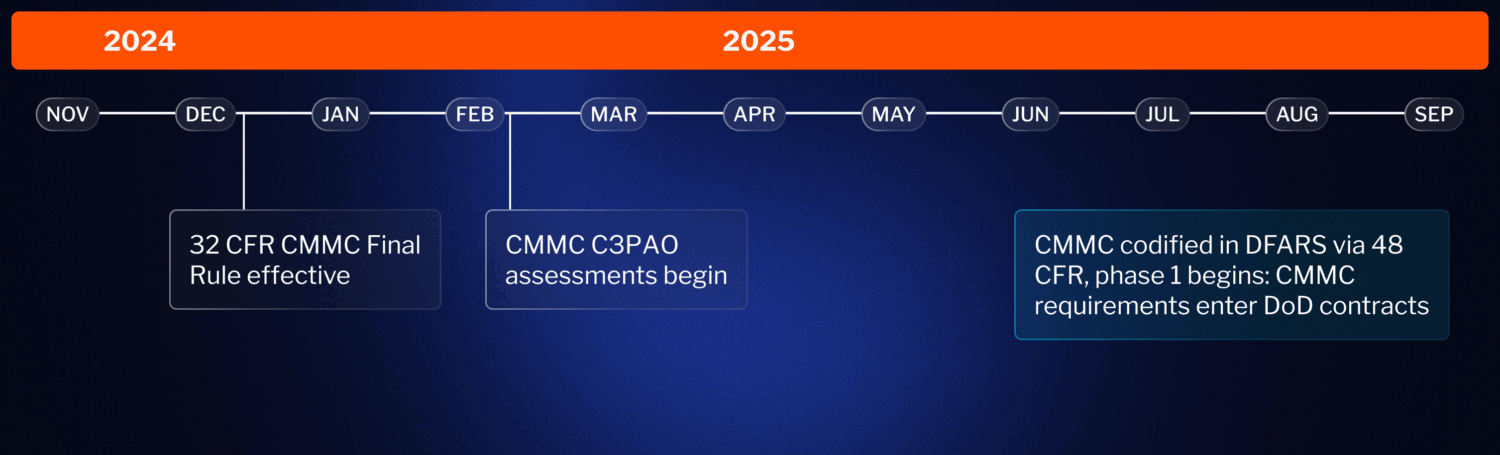
It’s important for contractors to understand that even though CMMC will be phased in over time, it does not necessarily follow that you have more time to achieve CMMC certification. Your organization, for example, could be far down the supply chain from a contractor subject to CMMC early on, in which case that contractor must flow down CMMC requirements to your organization at that point. As leading cybersecurity lawyer Robert Metzger noted at our 2024 CMMC Summit:
The problem for most contractors is that you won’t know in advance when the compliance requirement will come to you or when your Prime will ask you to show you are ready for a certification assessment. Most organizations find that it takes 6-18 months to know that you are ready to pass an assessment. So you need to get started now.
Informed estimates from cybersecurity companies that have completed audits are that it takes typical SMBs between 12 months to meet CMMC Level 2 requirements. That time frame exceeds estimates of how long it will be before CMMC requirements begin to appear in DoD contracts.
Now is the time to get started on CMMC certification.
CMMC Compliance Checklist
We’ve broken down your CMMC compliance journey into 12 straightforward steps. The goal is to help your organization achieve CMMC certification as efficiently and cost effectively as possible.
Step 1. Familiarize yourself with the CMMC framework
You’re off to a good start with this blog, and after reading it you may want to refer to PreVeil’s paper, Achieving CMMC Compliance: A guide for small and midsize defense contractors. Continue to stay on top of developments by regularly checking the DoD’s CMMC website and the Cyber AB’s website.
Step 2. Determine your CMMC level
Your defense contract will specify which CMMC level your organization will need to achieve. CMMC levels are based on the type of information your organization works with. Any organization that handles CUI will need to achieve at least Level 2.
If your contract is unclear about CMMC and whether you’re work entails handling CUI, then contact either your contracting officer or the organization above you in the supply chain to learn more.
Step 3. Ensure at least one person owns CMMC compliance
Dispersing responsibility too often results in no responsibility. Instead, assign a compliance point person to own your team’s compliance journey. This will often be someone in IT, but it doesn’t have to be.
Your compliance point person will need to meet with all the various stakeholders within your organization and ensure their participation and timely delivery of results. Full support of your executive team is critical for success. In fact, in addition to outside assessments every three years, CMMC also requires an annual attestation from a senior executive confirming their organization’s compliance at their required CMMC level—making them accountable in the eyes of DoD and the Department of Justice.
The compliance point person is also responsible for ensuring appropriate technologies are purchased, policies are created, and protocols for continuous improvement are followed.
Step 4. Scope your compliance boundary
Determine who in your organization accesses CUI; which devices process CUI; which organizational processes are related to the protection of CUI; and, importantly, how these users, systems and devices can be segregated into an enclave separate from the non-CUI part of your organization. Once you answer these questions, do your best to narrow your compliance boundary, or scope.
The size of the group with access to CUI will help determine how costly compliance is. Limit access to CUI to only those team members for whom access is critical to their work. Every person who has access will need to be trained on CUI management and will require licenses to compliant technologies. The fewer the people with access, the faster and cheaper it will be to conduct that training and secure those licenses.
One of the best or optimal solutions that I have seen for lowering CMMC costs is building an enclave. A secure enclave strategy basically allows you to build a technology infrastructure that is logically or physically separate from the business infrastructure. So you build that environment and you apply all the controls or whatever is applicable to that to make sure that environment is CMMC compliant. – Manas Das, StrategicIT
Similarly, the size of the enclave where CUI lives helps determine how costly it will be to achieve compliance. The smaller you can make your CUI enclave, the cheaper, faster, and easier compliance will be to achieve because you will have fewer endpoints to secure and fewer people to train on CMMC compliance protocols.
Step 5. Adopt a platform to secure CUI
Most organizations will need to employ new technology solutions to protect CUI. Remember that file sharing and email is how CUI is most often transmitted both inside and outside of an organization. If you’re using Microsoft 365 Commercial or Google Workspace, those communication systems cannot support CMMC compliance. You’ll need to make a switch.
Ask your current Cloud Service Provider (CSP), or ask any other vendors you are considering, the following key questions:
- How do you support the 110 security controls of NIST 800-171? NIST 800-171 was written specifically to protect CUI; compliance with it is required at CMMC Level 2. Your CSP needs to securely store, process and transmit CUI.
- Are you FedRAMP Moderate Baseline or Equivalent? Confirm the CSP has either a FedRAMP ATO (Authority to Operate), or that it has been certified as FedRAMP equivalent, as required for CMMC certification.
- If CUI is encrypted, do you have the required FIPS 140-2 certificate? CSPs that use encryption to protect CUI must submit their cryptographic modules to approved independent laboratories for extensive testing to obtain a FIPS 140-2 certificate. Without that, your CSP won’t help you achieve CMMC certification.
- Do you meet DFARS 252.203-7012 c-g for incident reporting?
Keep in mind that, ultimately, your organization is responsible for ensuring that your CSP and any other vendors meet the security requirements that it claims to.
Step 6. Develop robust documentation
It’s not enough to simply protect CUI, you also must be able to prove that you’re compliant. That’s accomplished with detailed documentation, which requires thorough and meticulous work to develop. The first task you’ll need to tackle is development of a System Security Plan (SSP) as mandated by NIST 800-171. The SSP explains how your organization meets each of NIST SP 800-171’s 110 security controls. The SSP is the foundational document for a NIST SP 800-171 assessment and is a prerequisite for consideration for any DoD contract.
The system security plan should be considered the overarching source of truth. It’s kind of like that single point of reference that …members of the organization’s team use to know who’s actually responsible for managing controls in their CMMC assessment program. It’s really where we go to first as a C3PAO to identify those organization defined parameters and what the organization has defined for itself. –Marci Womack, Schellman
Create your SSP early on in your compliance journey. It’s a living document and will change as you improve your cybersecurity and work towards NIST 800-171 compliance. You’ll also need a Customer Responsibility Matrix (CRM) from your CSP and any ESP (External Service Providers) if you have them. The CRM should show clearly which NIST 800-171 controls the CSP/ESP supports by either allowing the customer to inherit the control or objective from them, or by sharing the responsibility for the control or assessment objective with the customer.
Finally, you’ll need policy and procedure documents associated with each NIST 800-171 security control as well and, following your self-assessment (see the next step), Plans of Actions and Milestones (POA&Ms) for all controls not yet met.
Step 7. Conduct a self-assessment against NIST 800-171A
The only path to CMMC Level 2 certification is through NIST 800-171.Once you’ve adopted a platform to implement NIST 800-171’s security controls as best as you can on your own, and have developed your SSP and other key documents, you’re ready for your first NIST 800-171 self-assessment.
The self-assessment should be conducted according to the DoD’s Assessment Methodology, which is spelled out in NIST 800-171A (the A stands for assessment). The methodology specifies 320 objectives spread across the 110 security requirements. Every objective associated with a control must be met for that control to be satisfied. From there, each of the 110 NIST 800-171 security controls is assigned a weight of either 1, 3 or 5 points. Scoring starts at the highest possible score of 110. Points are deducted for each control not satisfied, all the way down to -203. Negative self-assessment scores are possible, as scores can range from +110 down to -203, a spread of 313 points.
You are also required to submit your self-assessment score to the DoD’s Supplier Performance Risk System (aka SPRS, and so the score is commonly known as an SPRS score). Your SPRS score must be updated at least once every three years.
Step 8. Create your POA&Ms and execute
Know that perfect scores of 110 are quite rare for NIST 800-171 self-assessments done early in your compliance journey. Your organization likely will have some controls that are unmet. Create POA&Ms for those items and specify the technologies and procedures you will use to close those gaps and by when a score of 110 will be achieved.
It’s important to note that once CMMC is in effect, POA&Ms will be permitted at CMMC levels 2 and 3 only for some one-point controls. At Level 2, with one exception, POA&Ms will not be permitted for any three- or five-point controls—which are some of the hardest requirements to meet.
Then execute your POA&Ms and close your security gaps. For now, there is no deadline for closing out your POA&Ms, but under CMMC, POA&Ms will be time-bound: organizations will have 180 days to close all the security gaps listed in their POA&Ms.
It is critical that organizations prioritize closing any security gaps revealed by their NIST 800-171 self-assessment.
Step 9. Update your documentation
Given all the work you’ve done, and no doubt how much you’ve raised your cybersecurity levels, it’s time to revisit the documentation you developed in Step 6 above. Update your most fundamental document, your System Security Plan (SSP), along with your Customer Responsibility Matrix (CRM) if necessary, any policies and procedures you may have changed and improved, and your Plans of Action & Milestones (POA&Ms).
Step 10. Conduct a CMMC Level 2 self-assessment
Now step back for an overview. Is your documentation of NIST 800-171 compliance thorough and accurate? How close to 110 is your NIST 800-171 self-assessment score? Do you think you can address the security deficiencies outlined in your outstanding POA&Ms in a timely fashion?
The answers to these questions will reveal your next move. If you don’t feel confident about moving forward to an outside assessment yet, then your best bet is to:
REPEAT STEPS 7 – 10 AS NEEDED
Once you’re satisfied with your own self-readiness assessment, your organization is ready to move on to the last two steps:
Step 11 (optional). Work with a partner for a final check
Your most cost-effective approach may be to hire a consultant who can help ensure your ultimate success by reviewing your documentation, checking your NIST 800-171 self-assessment score, and helping you close out your POA&MS. Working with a partner at this stage—or whenever you get stuck and need help—can help save you time and money by creating a smoother path to CMMC Level 2 certification. Note that the consultant or organization that helps you prepare for CMMC cannot also serve as the C3PAO that conducts your external assessment for CMMC certification.
The key is that you don’t take the next and final step—the high-stakes and potentially costly C3PAO assessment—until you’re as prepared as possible.
Step 12. Schedule your C3PAO assessment
You’ve gotten this far and are ready to move on to your third-party assessment! For CMMC Level 2 certification, those assessments are conducted by C3PAOs, who will start the process with their own review of your readiness. Assuming you’re ready to go forward—hopefully a safe assumption by now—they’ll check your documentation and will assess your compliance with NIST 800-171 based on NIST 800-171A (as you will have already done). There’s more, for example, employee interviews, and spot checks for artifacts such as records of training sessions, that prove compliance. Your organization is responsible for scheduling its C3PAO assessment. You can find a list of accredited C3PAOs on The Cyber AB Marketplace.
Learn more about how PreVeil can help
PreVeil’s proven solution can help you achieve CMMC Level 2 certification faster and more affordably. PreVeil is trusted by more than 1,700 small and midsize defense contractors and has been used by over 25 customers to achieve perfect 110/110 scores on DoD and CMMC assessments.