The International Traffic in Arms Regulations (ITAR), overseen by the Department of State, regulates the import and export of defense-related products listed on the United States Munitions List (USML). Compliance with ITAR is crucial for defense contractors and organizations managing these sensitive items, as they play a key role in protecting U.S. national security. Violating these regulations can lead to harsh penalties, including fines of up to $1 million per violation and imprisonment for up to 20 years.
In this blog, we’ll explore the key requirements for ITAR compliance, how to meet those requirements, the serious penalties of non-compliance, and strategies for protecting ITAR-controlled data.
Table of contents
ITAR Compliance Requirements You Need to Know
For organizations and their subcontractors aiming for compliance with the International Traffic in Arms Regulations (ITAR), understanding the key compliance requirements is the first step. Here is the list of requirements your operations needs to meet to ensure ITAR compliance:
1. Register with the Directorate of Defense Trade Controls (DDTC)
All entities covered by ITAR must file a Statement of Registration with the State Department’s Directorate of Defense Trade Controls (DDTC). This requirement holds whether you plan to export products, services, or data. Registrations must be renewed annually and may be denied due to legal issues or bans related to ITAR activities.
2. Restrict Access to U.S. Persons Only
The goal of ITAR is to control the import and export of technical data, including software, part-drawings, and photos, related to USML items. Organizations are only allowed to share ITAR data with US persons. U.S.-based companies operating overseas must not share ITAR-protected technical data with local employees unless specifically authorized by the State Department. Limited exemptions exist for certain allies like Canada, the UK, and Australia.
3. Adhere to Reporting and Record-Keeping Requirements
Comply with reporting and record keeping requirements. Organizations must report any ITAR violations to DDTC. Organizations must also retain records for five years after the completion of the transaction and make these records available to DDTC upon request.
4. Obtain Necessary Export/Import Licenses
Before exporting or importing defense-related articles or data, secure the appropriate licenses from the DDTC. These licenses, which can last up to four years, should detail the recipient, final use, end-user, and destination country of the items.
5. Monitor ITAR-Controlled Items
Maintain awareness of the location of ITAR-controlled items and who accesses them. Record all transfers, noting the specifics of each new custodian and any subsequent movements.
6. Ensure ITAR Compliance in Cloud Storage
ITAR imposes stringent controls on storing and handling defense-related data. Cloud providers must enforce robust security measures such as encryption, stringent access controls, and continuous monitoring to safeguard data. They must also comply with strict data residency regulations to ensure all ITAR-sensitive data remains within the U.S.
The United States Munitions List
- Firearms and Related Articles
- Guns and Armament
- Ammunition and Ordnance
- Launch Vehicles, Guided Missiles, Ballistic Missiles, Rockets, Torpedoes, Bombs, and Mines
- Explosives and Energetic Materials, Propellants, Incendiary Agents, and Their Constituents
- Surface Vessels of War and Special Naval Equipment
- Ground Vehicles such as tanks or infantry fighting vehicles
- Aircraft and Related Articles
- Military Training Equipment and Training
- Personal Protective Equipment
- Military Electronics
- Fire Control, Laser, Imaging, and Guidance Equipment
- Materials and Miscellaneous Articles
- Toxicological Agents, Including Chemical Agents, Biological Agents, and Associated Equipment
- Spacecraft and Related Articles
- Nuclear Weapons Related Articles
- Classified Articles, Technical Data, and Defense Services Not Otherwise Enumerated
- Directed Energy Weapons
- Gas Turbine Engines and Associated Equipment
- Submersible Vessels and Related Articles
- Articles, Technical Data, and Defense Services Not Otherwise Enumerated
Source: Code of Federal Regulations
ITAR Compliance Checklist
The U.S. Department of State leaves it up to manufacturers to develop, implement and maintain their own compliance programs. There is no specific ITAR certification to obtain, only your responsibility of registering with DDTC and being compliant.
Use this compliance checklist to guide your program.
- Start with ITAR Compliance Training. Understand how ITAR applies to your USML goods, services, or data, and make sure you are meeting ITAR requirements. First, review the USML list. All products and services related to items on the USML list are subject to ITAR. Next, familiarize yourself with all the articles of ITAR, which consist of 11 parts. The regulations are deliberately designed for flexibility, so that you can adjust your security practices to your specific risk profile, as well as evolving technologies and national security threats.
- Ensure all organizations in your supply chain are ITAR compliant. It is your duty to ensure that all parties you share ITAR data with, including subcontractors, comply with ITAR. As part of this, you must ensure that you do not share data with any foreign persons without appropriate licensure, and never with anyone on the prohibited countries list.
- There is no formal certification process to become ITAR compliant. Instead, there are certain standards that companies are expected to comply with.Unlike CMMC and other regulations, ITAR does not have a formal certification process. It is your responsibility to ensure that your data handling processes are secure and protect national security interests. The hefty penalties leveraged against companies in breach of ITAR in recent years prove companies must take ITAR compliance seriously.
- Understand if exemptions apply to your organization. ITAR exemptions are very specific. Types of exemptions include public domain exemptions, technical data exemptions, and temporary importation of defense articles exemptions. Understand if any exemptions apply to your organization to avoid running afoul of ITAR.
- Report any ITAR violations that occur. Should an ITAR violation occur, accidentally or intentionally, it is your responsibility to report it immediately to DDTC.
Who Needs to Be ITAR Compliant?
Any U.S. company, research lab or university that engages in either manufacturing or exporting defense articles or furnishing defense services on the USML is required to register with the DDTC and comply with ITAR regulations. These requirements also extend to the company’s subcontractors and supply chain. 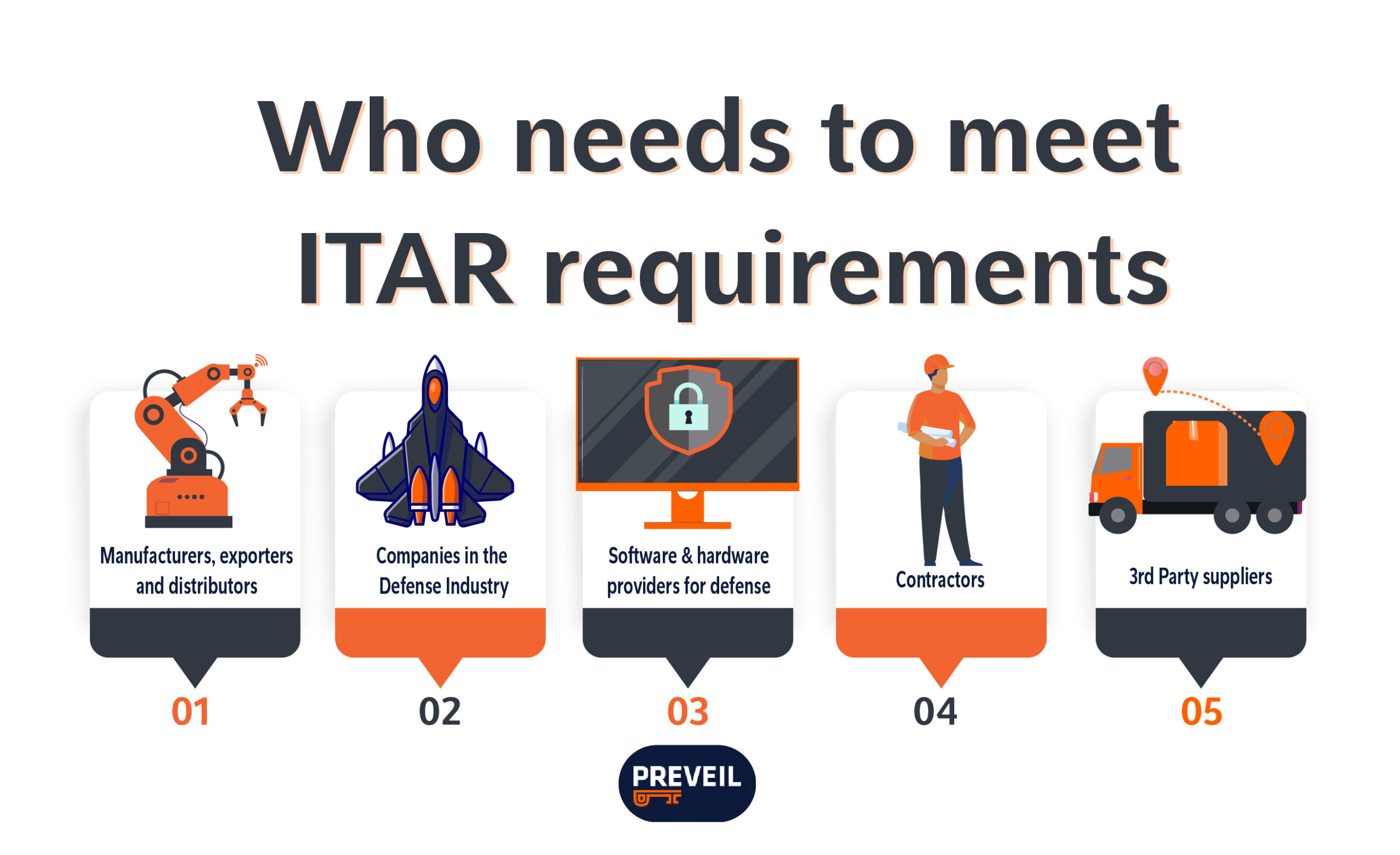
ITAR Violation Penalties
There are serious penalties imposed for failing to get the specific licenses and documentation required for ITAR compliance. These penalties can include civil fines of up to $500,000, criminal fines of up to $1,000,000, and jail time of up to 10 years imprisonment per violation.
Failure to Register: Manufacturing items listed on the U.S. Munitions List (USML) without proper registration is illegal.
Lack of Technical Data Licenses: Organizations must obtain appropriate approvals and licenses to export technical data or defense services related to firearms and ammunition.
Incorrect Documentation:Errors in documents, such as DDTC license applications or registration forms, can result in ITAR or customs violations.
Failure to Vet Other Parties: ITAR data must not be sent to parties that are barred from handling it.
Uncontrolled Technical Data: It is prohibited to transfer or disclose technical data to foreign persons within the United States without the required licenses.
Willful Non-compliance: Deliberate failure to adhere to ITAR regulations is taken especially seriously and may result in harsher penalties or additional charges.
ITAR Violation Example
Boeing Fined $51 Million for Multiple Violations of ITAR and AECA Regulations
The Boeing Company recently agreed to pay a $51 million civil penalty for violating U.S. export regulations, specifically the International Traffic in Arms Regulations (ITAR) and Arms Export Control Act (AECA). According to the DDTC, Boeing is guilty of:
- Unauthorized exports and transfers of controlled technical data to foreign-person employees and contractors
- Unauthorized exports to the People’s Republic of China
- Violation of export license terms, conditions and provisos present on DDTC export authorizations
- Failure to implement promised corrective actions
ITAR Encryption Carveout
Before March 2020, organizations were required to store all ITAR technical data on U.S.-based servers, managed by U.S. persons, primarily using on-premise storage solutions. However, in March 2020, the State Department acknowledged advances in cybersecurity that could enhance operations without jeopardizing national security. Consequently, they issued 22 CFR 120.54, also known as the ITAR Carveout for Encrypted Technical Data. This regulation allows defense companies to use end-to-end encryption to transmit, store, and share unclassified ITAR technical data without needing an export license, if they adhere to the following criteria:
- Data Classification: The data must remain unclassified.
- Encryption Standards: Data must be secured using end-to-end encryption compliant with FIPS 140-2 standards or its successors.
- Security Measures: The data must not be decrypted at any point from origin to recipient, nor can decryption means be provided to any third parties, including cloud service providers. This ensures that only the intended recipient, who must be a U.S. person or someone authorized under ITAR, has access to the decryption keys, network access codes, or passwords.
- Geographic Restrictions: The data must not be intentionally sent to or stored in countries restricted under ITAR regulations, nor sent from these countries.
The introduction of 22 CFR 120.54 allows organizations to shift from expensive on-premise data storage to more cost-effective, end-to-end encrypted cloud services. This update not only simplifies the management of ITAR data but also reduces the need for frequent import/export licensing for data sharing.
Download our ITAR Compliance Guide
ITAR Compliance Software
PreVeil’s Email and Drive platforms meet the rigorous requirements set by the State Department under the ITAR Carveout for Encrypted Technical Data. By leveraging state-of-the-art end-to-end encryption, PreVeil ensures that all user data remains protected throughout its lifecycle.
Robust Encryption Standards: At the core of PreVeil’s security architecture are FIPS 140-2 validated encryption algorithms. By relying on these algorithms, PreVeil is able to ensure that data is encrypted before leaving the user’s device and remains encrypted until it reaches the intended recipient; it is never decrypted on the server. This method effectively shields the data from unauthorized access, including from server attacks or insider threats.
Exclusive Access to Encryption Keys: Unique to PreVeil’s platform is the absolute control over encryption keys. No third party, nor any other organization, has access to the keys, network access codes, or passwords necessary for decryption. Only the recipient can decrypt the data, ensuring unparalleled security of sensitive information.
PreVeil Drive for Secure File Management: Users can encrypt, store, and share files containing ITAR-regulated data using PreVeil Drive. This platform integrates seamlessly with everyday tools such as Windows Explorer, Mac Finder, and web browsers, making it incredibly user-friendly while maintaining robust security.
PreVeil Email for Secure Communications: With PreVeil Email, users can continue to send and receive emails using their existing email addresses from services like Office 365, Gmail, or Apple Mail. The transition to using PreVeil’s encrypted email system is smooth and familiar, minimizing disruption and training requirements while enhancing the security of email communications.

