The CMMC Final Rule is now live and CMMC assessments are ongoing. CMMC will enter DoD contracts in mid-late 2025.
CMMC Background
Defense contractors handling controlled unclassified information (CUI) have been required to meet the 110 controls of NIST 800-171 since 2017. CMMC will validate compliance with NIST 800-171 through independent assessments conducted by C3PAOs (CMMC Third-Party Assessor Organization).
The DoD has made clear that CMMC is imminent and defense contractors need to work towards meeting compliance. Here’s what Matt Travis (CEO of Cyber-AB) warned at PreVeil’s CMMC Summit:
If you haven’t started getting engaged in CMMC, now is the time to do so. It was probably the time in early 2024, but now the light is flashing red.
The Latest CMMC Timeline
The CMMC Final Rule (CFR 32) became effective on Dec 16, 2024, and CMMC assessments started on Jan 2, 2025. CMMC will enter contracts (CFR 48) in mid-2025.
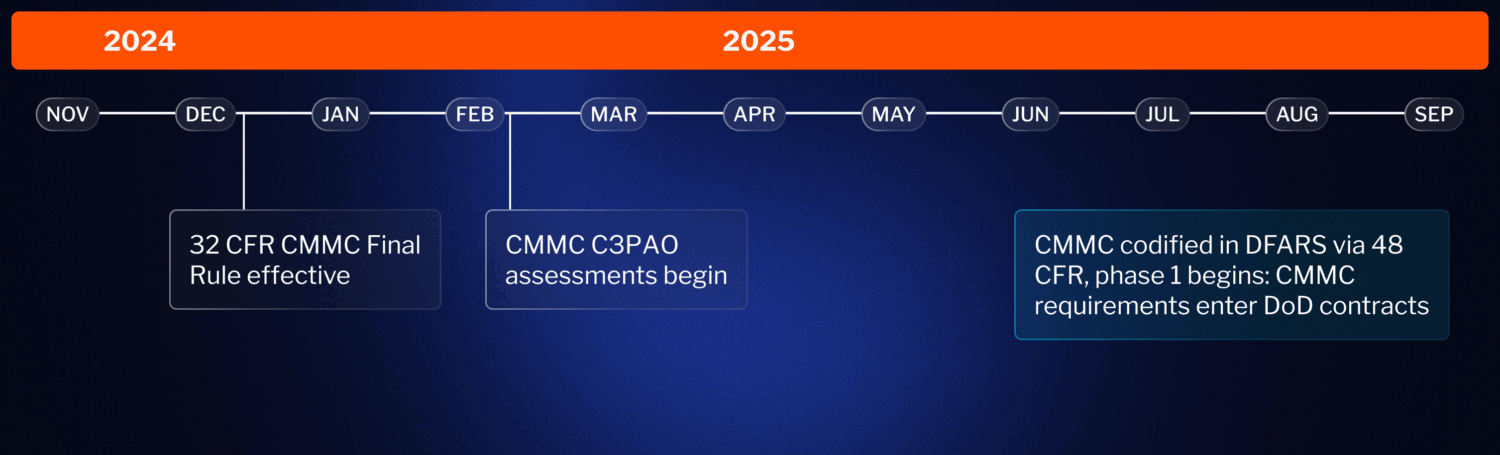
CMMC Compliance Deadline: When will it be in contracts?
The DoD Deputy Chief Information Officer (CIO) for Cybersecurity, David McKeown, said in June 2024 that “the DOD should be officially rolling CMMC 2.0 out and including it in contract paperwork in the first quarter of calendar year 2025”.
However, this does not mean that companies should wait to begin a CMMC implementation plan. NIST 800-171, which CMMC is based on, is already required today. Furthermore, Primes are already beginning to require their subcontractors to meet CMMC compliance requirements, ahead of the rule. Here’s what Leidos CISO JR Williamson said on a PreVeil panel,
Compliance isn’t going away. It is going to be a requirement to be able to bid on and continue to operate on these contracts.
Defense contractors who are not yet meeting all 110 NIST 800-171 controls should prioritize this immediately if they wish to continue bidding on defense contracts.
Preparing for CMMC Level 2
Given that CMMC will be in contracts in Q2 2025, you need to get started on your compliance preparations now, as it takes 12 months for the average defense contractor to get assessment ready. Doing nothing is not an option. Here’s what Matt Travis said:
If you do not get CMMC Certification, you will not be able to win DoD contracts. I cannot emphasize that enough
If you’re not sure where to start, read our CMMC Compliance Checklist blog. For convenience, here are a few ways to expedite your compliance journey:
1. Limit your Compliance Boundary with an Enclave: You may be able to establish a secure, isolated environment for CUI, which can simplify your documentation and save you money on licenses.
2. Use Pre-filled Documentation: Protecting CUI is at the core of NIST and CMMC compliance. However, you also must provide detailed documentation to prove that you’re compliant. CMMC assessments will be conducted by C3PAOs who will start by asking for this documentation. For example, your System Security Plan (SSP) needs to document how your organization meets the 110 controls of NIST 800-171.
3. Limit POA&MS: Plans of Actions & Milestones (POAMs) describe your plan to meet any controls that are currently unmet. Make sure you are taking steps to address any POAMs and specifying the technologies and procedures you will need to close those gaps. C3PAOs will allow for only a limited use of POAMs at the time of assessment and then only for the least critical controls. You will need a minimum score of 80% (88/110) to be eligible for a conditional certification so we do not recommend relying on POAMs to pass CMMC.
4. Leverage Partners: If you get stuck, or don’t have the time or expertise to complete the steps required, you can take advantage of PreVeil’s preferred network of Assessors, Consultants, and Service Providers. They offer a variety of services to help accelerate your compliance journey, and you can have confidence that they were vetted and recommended by the PreVeil compliance team.
According to the current letter of the law, NIST 800-171A, you are already responsible for meeting all of the security standards included in CMMC. If you are not yet fulfilling this obligation, the time to act is now.
Next Steps
The goal for defense contractors is to not only remain eligible to win defense contracts, but also to minimize business risk and protect CUI from our country’s adversaries. By getting started on your organization’s compliance journey, you can achieve these objectives and ensure your company is ready for ramped-up federal enforcement of cybersecurity regulations.
Learn More: Case Study: Defense Contractor Achieves CMMC Compliance with Perfect 110 Score