For defense contractors, a Plan of Actions & Milestones (POA&M) is a critical tool for demonstrating progress toward meeting cybersecurity requirements like NIST 800-171 and CMMC. In this blog, we’ll break down what a POA&M is, why the DoD relies on it, and how contractors can use it to strengthen compliance efforts, satisfy assessors, and stay competitive for defense contracts.
What is a POA&M?
A Plan of Actions & Milestones (or POA&M) is a document used to identify and track the remediation of security controls that are unmet by contractors seeking compliance. Defense contractors seeking compliance with NIST 800-171 and CMMC must have a System Security Plan (SSP) that describes the technologies, policies and procedures they are implementing to meet the 110 NIST controls. If any controls are unmet, they are required to create a POA&M.

It’s important to note that POA&Ms are not a loophole out of compliance. They buy you time to meet unmet controls, but in the end, you still need to meet them. Department of Defense (DoD) regulations for CMMC explain that contractors will have 180 days to close those gaps. To learn more about Plans of Action and Milestones, watch below.
CMMC & POA&Ms
Cybersecurity Maturity Model Certification (CMMC) will begin appearing in contracts on November 10th, 2025.. CMMC imposes restrictions on the use of POAMs to achieve CMMC certification:
- No POA&Ms will be permitted for defense contractors required to achieve CMMC Level 1. Contractors that handle Controlled Unclassified Information (CUI) and are subject to NIST 800-171 must achieve at least CMMC Level 2. POAMs will be permitted at CMMC Level 2, but only for some one-point controls in NIST 800-171. With one exception, POAMs will not be permitted for any three- or five-point controls—which are some of the hardest requirements to meet.
- Contractors can continue to move forward with the Level 2 certification process only if upon their initial third-party CMMC assessment they: 1) meet at least 80% of all the NIST 800-171 controls (which CMMC Level 2 requirements mirror), and 2) all controls not met upon initial assessment are permitted to be met via POAMs.
- Finally, POAMs will be time-bound under CMMC. Defense contractors will have 180 days to close them out in their SSP. If you don’t meet that deadline, you will have to go back to the drawing board and start the CMMC certification process over. Given that hard deadline, your best bet is to close out as many of your POAMs as possible before contacting a C3PAO (CMMC Third Party Assessment Organization) to conduct your CMMC assessment. Note that it will be up to your C3PAO to approve your use of POAMs to achieve compliance; if you’re too far off target, you may not get that go-ahead.
DoD’s allowance for POAMs is a good-faith admission that getting an organization to compliance takes time and effort. POAMs offer a way for organizations that have achieved most of their compliance objectives to remain competitive for contracts while they finish closing out their last few unmet controls.
How to Make a POA&M
To create a POA&M that is as effective and useful to a C3PAO as possible, it should include the following essential elements:
- Indicate the NIST 800-171 control to which it applies: This component indicates the specific NIST control and objective that is not currently being met by the contractor
- Person of contact (POC) responsible for actions: This indicates the person(s) responsible for ensuring it is remediated.
- Actions and resources needed for remediation: This section will indicate the actions and resources needed to resolve the vulnerability. The resources in this case could be technologies or individuals
- Intended action start and completion dates: Contractors will indicate the intended start and completion dates for resolving the POAM
- Actual action(s) taken: This section provides a listing of the actions taken to resolve the vulnerability
- Milestones to meet: Here, the contractor provides a high-level overview of the actual steps taken to resolve the POAM
- Current status of efforts to meet the control: This last column is used to indicate where the contractor is in remediating the issue.
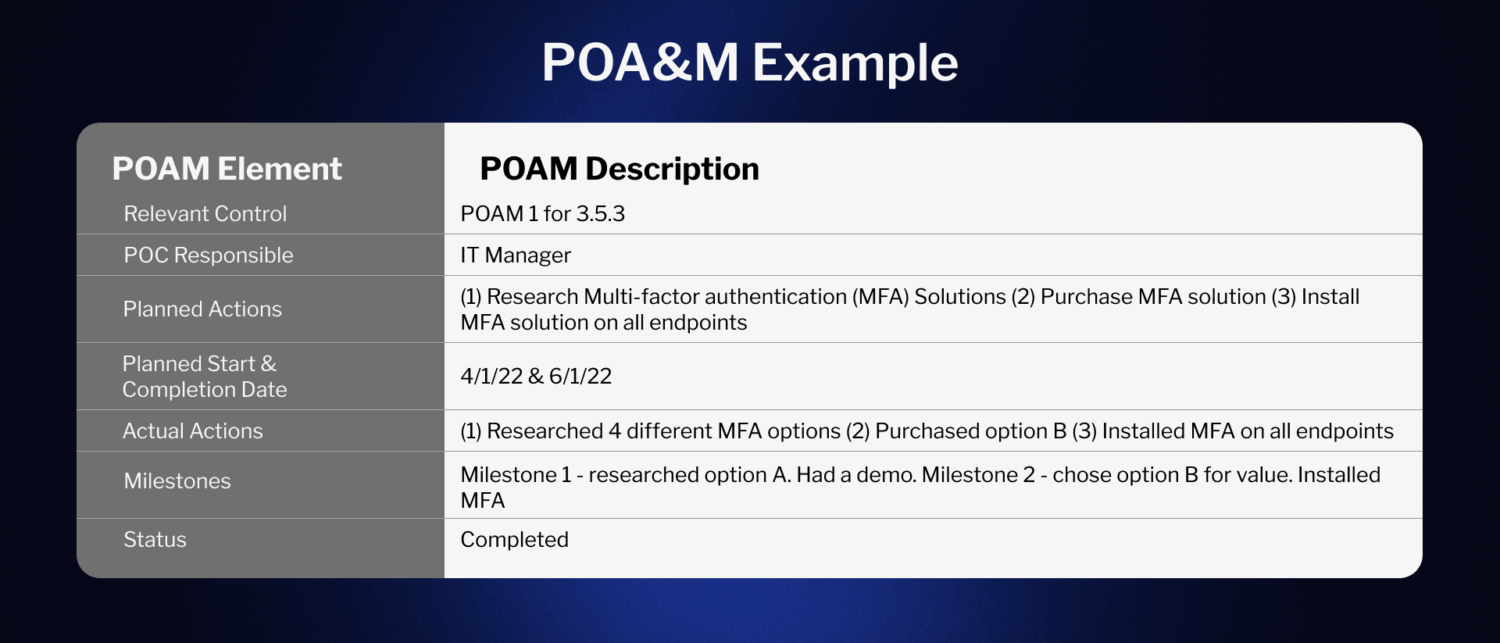
POA&M Example
Below is an example of how to make a POA&M. While you can make yours more complex, this demonstrates 7 key elements that a basic one should contain:
POA&M Template
PreVeil has created POAM a template to help defense contractors. PreVeil’s template shows how controls that PreVeil doesn’t support can be met. Contact PreVeil for a copy. You can also cut down up to 60% of documentation work with PreVeil’s Compliance Accelerator solution. It includes a POAM worksheet that lists the controls and assessment objectives that are out of scope for PreVeil and provides suggestions and examples for how to address them.
Recall that under CMMC, POA&Ms will be accepted only for eligible 1-point controls. Any POA&Ms PreVeil provides for ineligible controls are solely to guide your compliance preparations. Further, you should strive to close your POA&Ms for even the 1-point controls prior to assessment in order to have the best chance of success in the process.
POA&M Template Example
Here you can download the POA&M template example for AC (Access Control) L1-3.1.22, which stipulates that information posted on or processed on publicly accessible information systems must be controlled—lists each of the eight assessment objectives associated with that control. The objectives guide you through each step it takes to meet the control.
POA&M FAQs
What is the required timeframe to remediate POA&M items in a defense contract environment?
Defense contractors are often required to close POAM items within 180 days of the assessment. If items remain open past this window, it can jeopardize certification/status.
Can a POA&M evolve over time?
Yes, a POA&M is intended to be a living document, not static. As new deficiencies emerge or priorities shift, entries can be added, updated, reprioritized, or closed. But changes should be well documented and defensible, especially during audits.
Are POA&Ms unique to CMMC / NIST 800-171, or used in other federal frameworks?
POAMs are common across many federal and cybersecurity compliance frameworks (e.g. FISMA, FedRAMP, RMF) to handle identified security weaknesses and map out remediation plans. But each program may impose specific requirements on how POA&Ms are used, tracked, or limited.
Does having a POAM weaken the credibility of your compliance posture?
Not inherently. If done right, a POA&M can strengthen your posture by showing transparency, planning, and accountability. However, overreliance on it (i.e. leaving many critical controls unresolved) may raise red flags to auditors or DoD evaluators.
Conclusion
POA&Ms can be helpful for contractors that have made a good faith effort to meet NIST 800-171 and CMMC Level 2 requirements, but still need time to fully meet some 1-point controls. They grant you an extension, but your best strategy should be to think of them primarily as a roadmap to closing out controls.
Schedule 15 Minutes for free with our Compliance team
Book a session with PreVeil’s compliance team to see PreVeil’s SSP and POAM templates and get your compliance questions answered.
Learn More about Creating a POA&M and Compliance:
PreVeil has numerous resources to help you on your compliance journey, for example:
- A Guide to Achieving CMMC Compliance
- 6 Ways to Save Money on CMMC Certification Costs
- PreVeil case studies
Or, summarize in AI: