If you’re a defense contractor handling Controlled Unclassified Information (CUI), then your contract will have a DFARS 252.204-7012 clause in it that requires you to protect that sensitive information. While that may seem clear enough, in practice it’s common for defense contractors to work with other contractors in their supply chain, Managed Service Providers, Cloud Service Providers (CSPs), and others, in support of their DoD work. Understandably, all those players can muddle the answer to the question: Who’s responsible for protecting CUI?

What Is Controlled Unclassified Information (CUI)?
CUI is information that the Federal government creates or possesses, or that an organization creates or possesses on behalf of the Federal government that requires safeguarding or dissemination control. To be clear, CUI is not classified information. (Remember, the “U” in “CUI” stands for unclassified.)
For the government, CUI falls into two possible categories —CUI Basic and CUI Specified. CUI Basic is a type of CUI that requires the information be protected but does not have specific handling or dissemination controls. CUI Specified however is information that does have specific controls for handling or dissemination.
All CUI is considered at least Basic and must be protected per NIST 800-171 requirements. But some CUI requires dissemination controls and enhanced physical safeguards beyond NIST 800-171; that type is labeled CUI Specified.
Examples of CUI
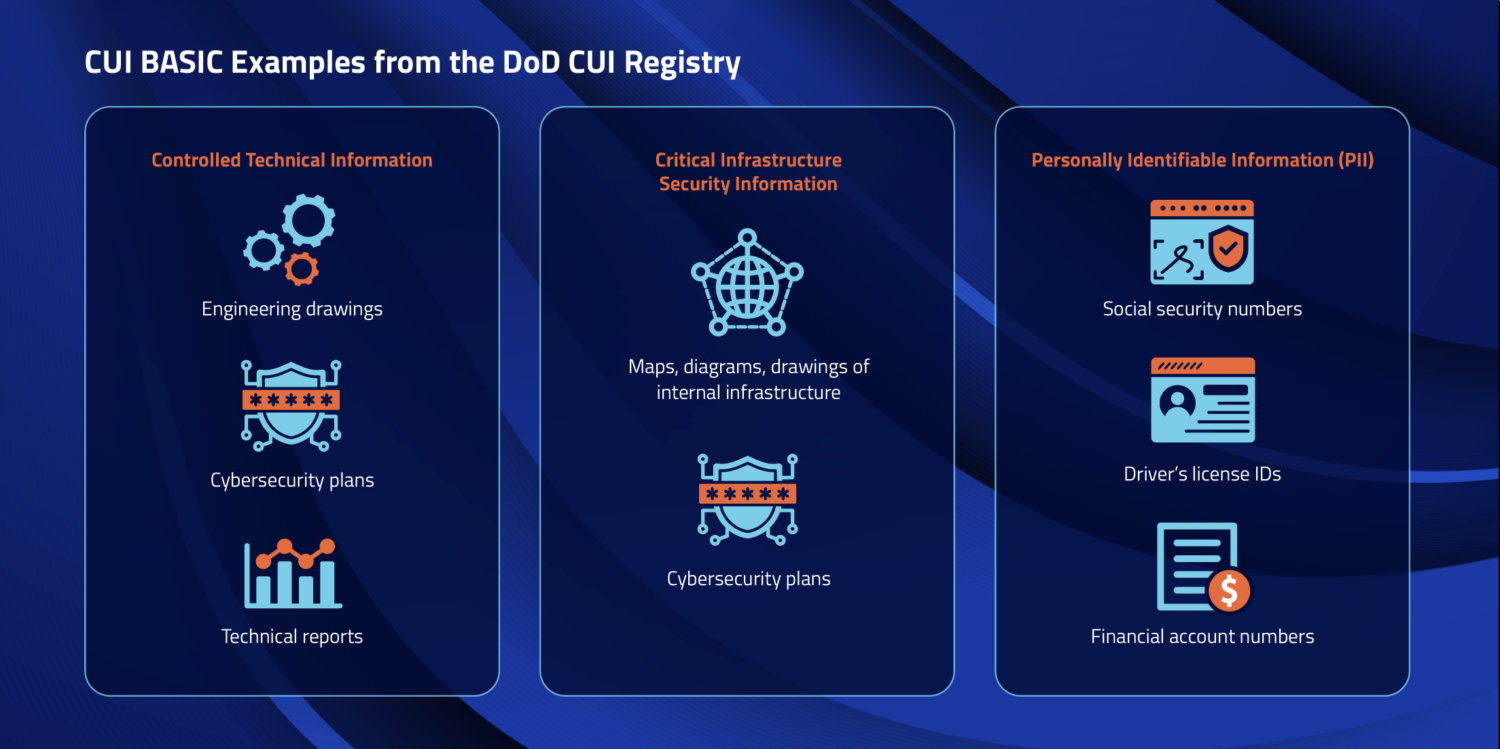
CUI Basic includes the broad categories of DoD Critical Infrastructure Security Information, Personally Identifiable Information (PII) and Protected Health Information (PHI). Basic CUI does not require any additional protections by contractors beyond the baseline protection for all CUI. The image below has further examples of each category.
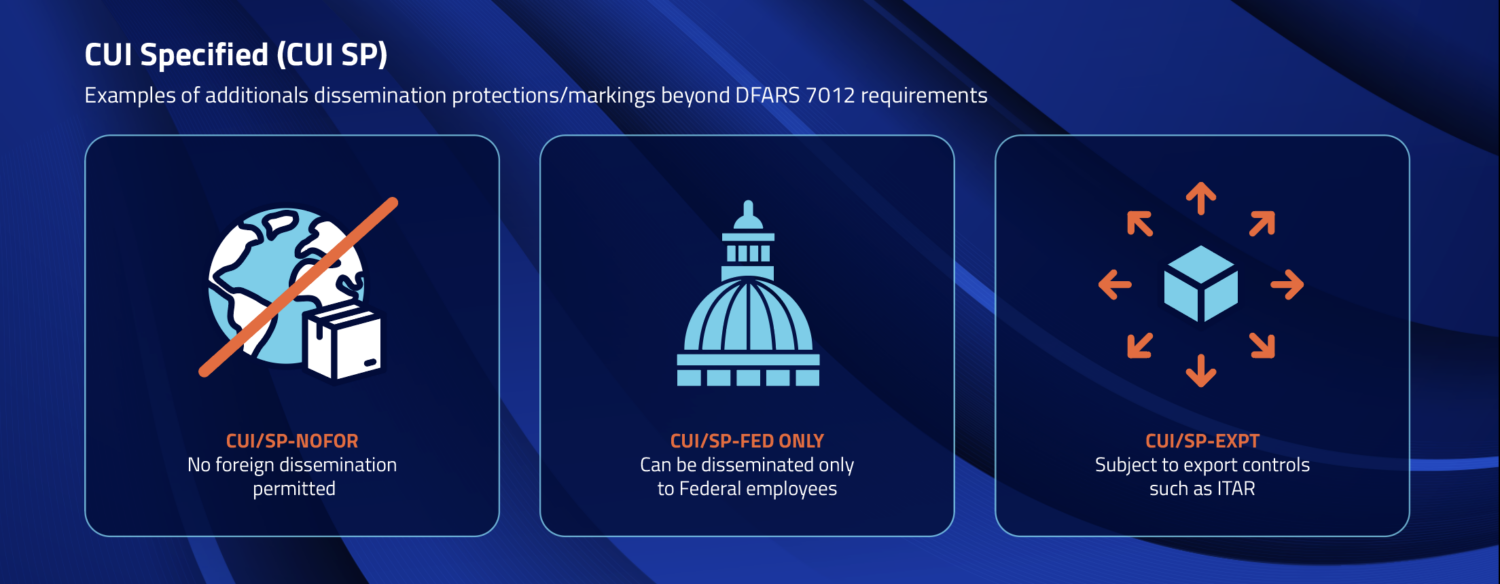
CUI Specified includes information that has specific handling or dissemination controls. ITAR data is an example of CUI Specified. Other examples include critical infrastructure information or Personal data such as social security numbers.
Minimum CUI Marking Requirements
Emails containing CUI require a banner marking on the top portion of the email. In addition to the banner marking, an indicator can be included in the subject line to indicate that the email also contains CUI.
Documents, slides and other file types containing CUI must also be marked to identify they contain this type of information. See the National Record Archives for specific steps to follow for proper marking.
Who Is Responsible for Applying CUI Markings?
The Federal agency that your organization has a contract with (as either a prime or subcontractor) is responsible for marking or identifying any CUI shared with non-Federal entities. The CUI must be marked consistent with the National CUI Registry, and the agency designating the CUI must make recipients of the CUI aware of the fact that they are receiving CUI. For our purposes, the responsible Federal agency is the DoD.
At times though, CUI is not labeled and it is unclear what kind of protection is needed. If the government has not labeled the information as CUI but a contractor suspects it might fall under the CUI category, then they should check with their Prime or KO (contracting officer).
| Email containing CUI | Document containing CUI |
Who Is Responsible for Protecting CUI?
Check your contract to see if it contains a DFARS 252.204-7012 clause. If it does, then your contract work entails handling CUI. And if that’s the case, then regardless of any other organization you may work with to fulfill your contract, the bottom line is that you’re responsible for protecting that CUI.
That means, for example, that if you hire an Managed Service Provider or Cloud Service Provider to manage your IT infrastructure or provide cloud storage, then you are responsible for confirming that those providers can adequately safeguard CUI per DFARS 7012 requirements. (See more on this below.)
If you have any questions about the status of the information shared with you as part of your DoD work, ask the organization that gave you the information about it. Sometimes, for example, you may receive CUI that isn’t properly marked as such. Therefore, it is also your responsibility to be informed enough about at least the broad CUI categories listed in the NARA National CUI Registry (and mirrored in the DoD’s CUI Registry) so that you know when to ask questions.
Best Practices for Protecting CUI
DFARS 7012—entitled Safeguarding Covered Defense Information and Cyber Incident Reporting—stipulates the cybersecurity requirements that contractors handling CUI must meet to safeguard the defense information they handle. DFARS 7012 does not apply to contractors who supply only Commercial off the Shelf (COTS) items to the DoD, such as medicine or fuel that’s readily available in the same form to the public.
Here are some best practices for ensuring that CUI is kept safe:
- Provide adequate security to protect unclassified Covered Defense Information (known as CDI, a term that encompasses CUI).
Contractors must implement the 110 security controls stipulated in the National Institute of Standards and Technology (NIST) Special Publication (SP) 800-171 in order to provide adequate security. If encryption is used to protect CUI, then NIST SP 800-171 requires the use of FIPS 140-2 validated cryptographic modules. Note that the use of FIPS approved algorithms is not sufficient to meet this requirement. Rather, contractors must ensure those modules are FIPS validated modules as well. NIST maintains a list of vendors that use FIPS 140-2 validated cryptographic modules.; PreVeil is on that list here.
- Rapidly report cyber incidents to the Department of Defense Cyber Crimes Center (DC3).
Contractors must report cyber incidents to DC3, and must share all cyber incident data requested by D3C, retain that data for 90 days, and assist DC3 with any follow up investigations as needed. See PreVeil’s blog on DFARS 7012 (c)-(g), which specify these requirements.
- Meet Federal Risk and Authorization Management Program (FedRAMP) standards
Contractors must confirm that their CSP has achieved the FedRAMP Baseline Moderate or Equivalent standard. PreVeil has achieved FedRAMP Moderate Equivalent status and is the first CSP to do so.
- Provide employees with training to ensure proper protection of CUI
All employees who handle CUI must receive training on how to properly manage and handle that information. This training should focus on areas such as:
- Insider Threat Training
- Role based training & CUI Awareness
- CUI awareness and protection training
- Compliance educational awareness
Note that the DFARS 7012 clause also requires defense contractors to flow down all the 7012 requirements to their subcontractors.
Consequences of Failing to Protect CUI
Compliance with DFARS 7012 is not optional. If your organization fails to provide adequate security to protect CUI as required by DFARS 7012, you raise the risk of exposure to cyberthreats and ransomware attacks. Cybercriminals know that smaller organizations are often more vulnerable than higher-resourced prime contractors and so don’t hesitate to go after easier targets. The potential result is loss of your organization’s IP and its ability to operate, as well as the burden of associated recovery costs, including possibly a ransomware payment.
Moreover, the loss of DoD information has serious consequences: DFARS 7012 requires that all cyber incidents be reported to the DoD. If the ensuing investigation reveals a lack of adequate security—i.e., failure to comply with your DFARS 7012 contract clause—then the DoD may consider that a breach of contract and can take several possible corrective actions.
CUI: A preferred target for US adversaries
How PreVeil Helps Protect CUI
If your organization is responsible for protecting CUI, PreVeil can help. PreVeil Drive and Email are designed to secure, store and share CUI. They deploy easily as a complementary system, with no impact on existing file and email servers—making configuration and deployment simple and inexpensive. Users keep their regular email address, which keeps it simple for users.
Upon deployment, organizations will be well on their way to DFARS 7012 compliance, because PreVeil:
- Supports 102 of the 110 NIST SP 800-171 controls, and 260 of the 320 objectives that guide both self- and independent assessments of NIST SP 800-171 compliance
- Complies with DFARS 7012 c-g cyber incident reporting requirements
- Uses FIPS 140-2 validated modules for encryption
- Meets FedRAMP Baseline Moderate Equivalent standards.
Not only is PreVeil the first Cloud Service Provider (CSP) to meet the Department of Defense’s (DoD) stringent FedRAMP Moderate Equivalency requirement for CMMC and DFARS 7012 compliance, PreVeil has enabled over 50 customers to achieve CMMC compliance- validated by a perfect 110 score on their C3PAO or DoD assessment. In addition, PreVeil is used by over 2,000 defense contractors and provides a comprehensive solution to expedite CMMC compliance. In addition through a combination of inherited and shared controls, PreVeil supports over 90% of the NIST SP 800-171 security controls (102 of the 110).
If you need to hire outside help to meet your remaining obligations, PreVeil can offer help via its partner network of certified MSPs, consultants, and leading organizations and individuals, all with expert knowledge of DFARS and NIST (and CMMC too).
Next Steps
If you need help or have questions about protecting CUI, DFARS 7012, NIST SP 800-171, or any other topics, please don’t hesitate to reach out and schedule a free 15-minute consultation with PreVeil’s compliance team.
You also may wish to learn more by reading:
- Guide for SMB Defense Contractors to Achieve CMMC Compliance
- Case Study: Defense Contractor achieves CMMC compliance with perfect 110 score
FAQs about CUI Protection
What level of system and network is required for CUI?
Moderate. DoD contracts stipulate that suppliers must track CUI internally and communicate classifications to their DoD contract officer. CUI will be classified at a “moderate” confidentiality level consistent with instructions DoDI 8500.01 and 8510.01 within all DoD systems (source)