CMMC (CFR 32) went into effect December 16, 2024. This introduces several important changes for defense contractors who handle CUI and must achieve CMMC Level 2 certification. If your organization handles CUI, here’s what you need to know.
Key Points
- CMMC Level 2 assessments are now live and will be conducted solely by Cyber-AB authorized C3PAOs. DIBCAC will not play a role in these.
- Third-party assessments will be required for the majority of organizations seeking CMMC Level 2, ensuring they protect CUI according to the 110 controls of NIST SP 800-171 Rev2.
- A minimum score of 88 is necessary for conditional compliance certification, with limited flexibility for deferring certain controls through Plans of Action and Milestones (POAMs).
- The rule outlines the compliance obligations for Cloud Service Providers (CSPs) and External Service Providers (ESPs), such as Managed Service Providers (MSPs), that are used by Organizations Seeking Certification (OSCs) to meet CMMC compliance standards.
- A phased rollout of CMMC contract requirements begins as early as Q2 2025, gradually increasing the number of contracts mandating compliance.
- Organizations must establish a rigorous program based on the NIST 800-171 framework, including thorough documentation such as System Security Plans (SSPs), to demonstrate compliance.
Want to skip the details & get help? Our sales team can walk you through the steps you need to take, or schedule a free 15 minute call with our compliance team.
CMMC Timeline and Rollout
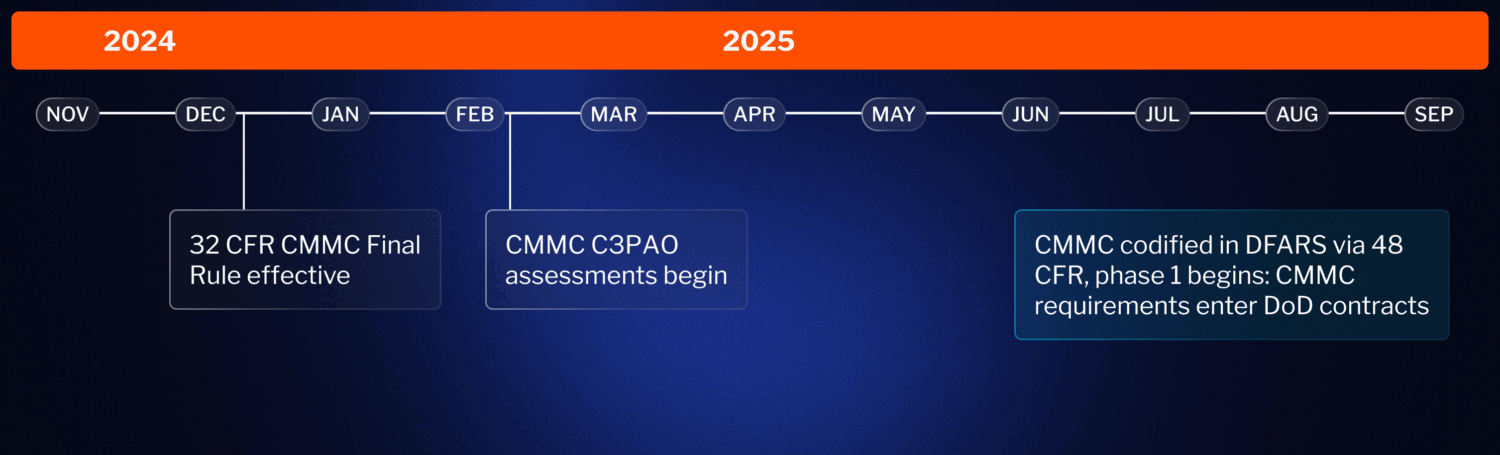
The CMMC program will enter contracts in four phases starting in Q2 2025. Each phase will last a year:
- Phase 1 (2025): DoD will begin requiring CMMC level 2 compliance in some contracts. Organizations wishing to participate in these contracts will either need to self-certify that they meet CMMC Level 2 or may be required by DoD to obtain C3PAO certification.
- Phases 2-4: The number of contracts requiring Level 2 compliance will increase, with all applicable contracts mandating CMMC certification by Phase 4.
Why Defense Contractors Should Start on CMMC Now
CMMC becoming effective brings a new urgency for defense contractors to act quickly, driven by 3 key factors:
- Contract Modifications Are Coming. DoD has made it clear that CMMC requirements may be added to existing contracts and renewals as early as mid-2025. Organizations that delay their preparation risk losing existing business relationships and future opportunities.
- Prime Contractors Are Already Requiring Compliance. Prime contractors aren’t waiting for official deadlines. They’re actively evaluating their supply chain’s compliance status to avoid disruptions & meet DFARS flowdown requirements. As JR Williamson, CISO of Leidos, explains, “We do run the risk that we may have a really great supplier that has a perfect solution…but they are not certified and not going to be certified for another 12-14 months. As a result, we just cannot use them and they’re off the team because we run the risk of not winning if they cannot be certified at the time the award is given.”
- Early Certification as a Competitive Advantage. As Robert Metzger notes, “There’s an advantage to getting under way already… CMMC level 2 certification assessments started after December 16th will count, giving you several years of coverage where you can show your Prime or the government that you are ready. It will be a positive competitive discriminator.”
Key Requirements for Organizations Seeking CMMC Level 2 Compliance
1. Meet NIST 800-171 Requirements
OSCs must implement all 110 NIST 800-171 controls to safeguard CUI. Key focus areas include access control, incident response, and physical security.
2. Achieve a Minimum Score of 88
While organizations may defer some non-critical, 1-point controls, the ability to use POAMs is limited and those POAMs must be completed within 180 days. Most controls must be fully implemented before certification can be achieved.
3. Cloud Service Providers (CSPs)
If an OSC uses a CSP to store, process, or transmit CUI, the CSP must meet FedRAMP Moderate Baseline Equivalent requirements as specified by the DoD in its December 21, 2023 equivalency memo or have an official Authorization to Operate (ATO). CSPs that only provide services categorized as Security Protection Assets are exempt from FedRAMP requirements but will fall within the organization’s compliance boundary and be subject to their assessment.
4. External Service Providers (ESP)
If External Service Providers (ESPs), such as Managed Service Providers (MSPs), deliver services that function as Security Protection Assets—like SIEM services, antivirus, or multi-factor authentication (MFA)—those services will fall within the organization’s compliance boundary and be subject to assessment. In these cases, the MSP is not required to obtain a separate CMMC certification, as the responsibility for compliance lies with the organization utilizing those services.
5. Flow-Down Requirements for Subcontractors
CMMC imposes flow-down obligations, meaning all subcontractors handling CUI must adhere to the same cybersecurity standards as prime contractors, ensuring protection throughout the supply chain.
6. Virtual Desktop Infrastructure (VDI) Clarifications
The final rule clarifies that host computers accessing and displaying CUI from a CMMC-compliant VDI environment via Keyboard, Video, or Mouse (KVM) may be considered out of scope for CMMC assessments. However, the VDI configuration itself is in scope and must comply fully with CMMC, including meeting applicable endpoint controls.
Achieving Compliance
Organizations seeking CMMC Level 2 compliance must focus on two key initiatives:
- Implementation of IT Systems and Policies
OSCs must implement and secure IT systems to protect CUI, following the NIST SP 800-171 framework. This includes putting in place cybersecurity practices and ensuring continuous monitoring. - Robust Documentation
Accurate documentation is crucial, with the System Security Plan (SSP) serving as the core document demonstrating compliance. The Customer Responsibility Matrix (CRM) also plays a key role, outlining shared responsibilities between the OSC and CSP/ESP. Regular updates to the SSP will be essential to maintain contract eligibility, as only a limited number of controls can be deferred through POAMs.
Regulatory Implications for OSCs
The era of deferring compliance is over. OSCs must now strategically prepare for CMMC requirements to maintain eligibility for future contracts. Key points include:
- Prepare for CMMC Now
Organizations should not delay preparation, as the regulation clarifies that the DoD may modify existing contracts or renewals to require CMMC compliance. - C3PAO CMMC Assessments are Live
For those ready, third-party assessments can help demonstrate competitiveness in contract bids. For others, a rigorous self-assessment is the first step, followed by third-party certification once they are confident in meeting the 88-point threshold.
Conclusion
The CMMC Final Rule introduces a significant shift in cybersecurity expectations for defense contractors. By preparing now, organizations can position themselves for success in future contract opportunities. Developing a comprehensive cybersecurity program and maintaining accurate, up-to-date documentation are critical steps for compliance.
Next Steps
If your organization wishes to stay in the Defense Industrial Base, then you will need to become CMMC compliant. PreVeil can help.
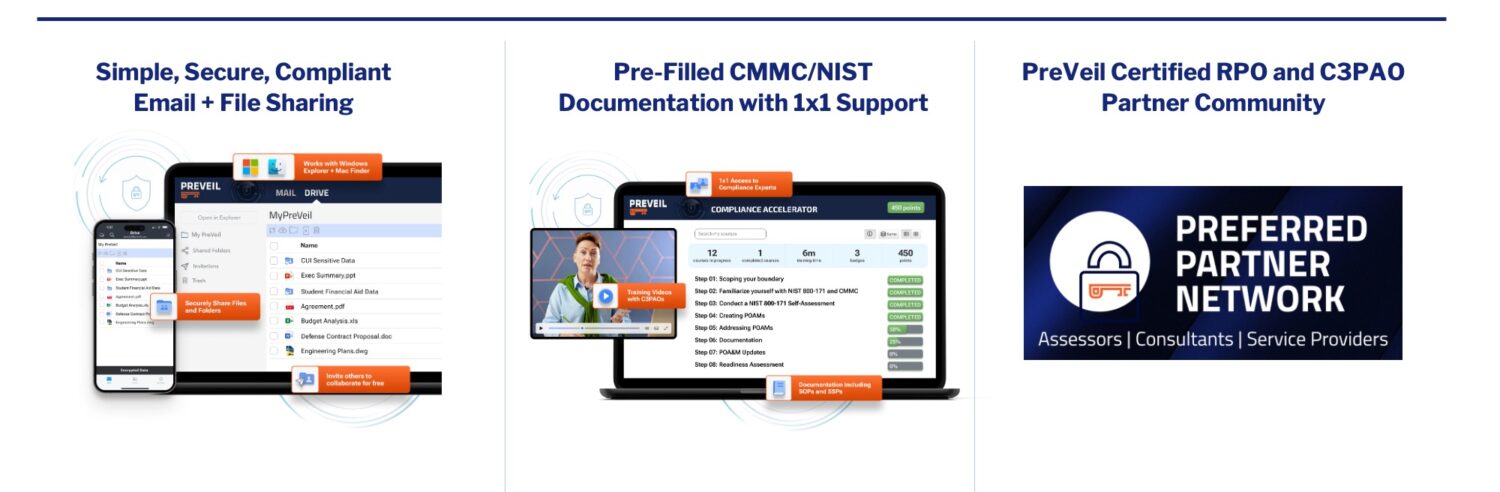
PreVeil is used by over 1,700 defense contractors and provides a comprehensive solution to expedite CMMC compliance. It includes:
- Technology Platform: Our Email and Drive platform protects CUI with end-to-end encryption and meets FedRAMP Moderate Equivalent, FIPS 140-2 and DFARS 7012 c-g.
- Compliance Accelerator: We provide pre-filled CMMC documentation, assessor-validated videos and 1×1 support from our compliance experts.
- Partner Network: We support your organization through the entire compliance journey – from prep to assessment – with our network of CMMC consultants and auditors.
PreVeil’s proven solution has been used by 25 defense contractors and C3PAOs to achieve perfect 110 scores in CMMC and DoD assessments.
To learn how PreVeil can help, reach out to our sales team.