If you are a government contractor handling Controlled Unclassified Information (CUI), compliance with NIST 800-171 is mandatory. The NIST 800-171 framework outlines 110 security controls designed to protect CUI. Since 2017, defense contractors in particular have been required to implement these controls, but until now, they were allowed to self-assess their compliance. That changed with the launch of the Department of Defense’s (DoD) Cybersecurity Maturity Model Certification (CMMC) program in January 2025 which now mandates third-party assessments to verify adherence to NIST 800-171.
This blog explains what defense contractors need to know about NIST 800-171, which may also be referred to as NIST SP (Special Publication) 800-171, and ways to make achieving compliance simpler + more affordable.
Table of contents
What is NIST 800-171?
NIST SP 800-171 is a set of guidelines published by the National Institute of Standards and Technology (NIST) for protecting the confidentiality of CUI. Defense contractors must follow these guidelines to ensure they can securely handle defense-related information in their contracts. Organizations within the supply chain for the DoD, General Services Administration (GSA), NASA, and other federal agencies must implement these security requirements if they handle CUI.
What is CUI?
Controlled Unclassified Information (CUI) is sensitive information created by or on behalf of the federal government that must be protected under specific laws, regulations, or policies. While CUI is not classified, its unauthorized disclosure can pose risks to national security. NIST 800-171 was developed to ensure this data remains secure.
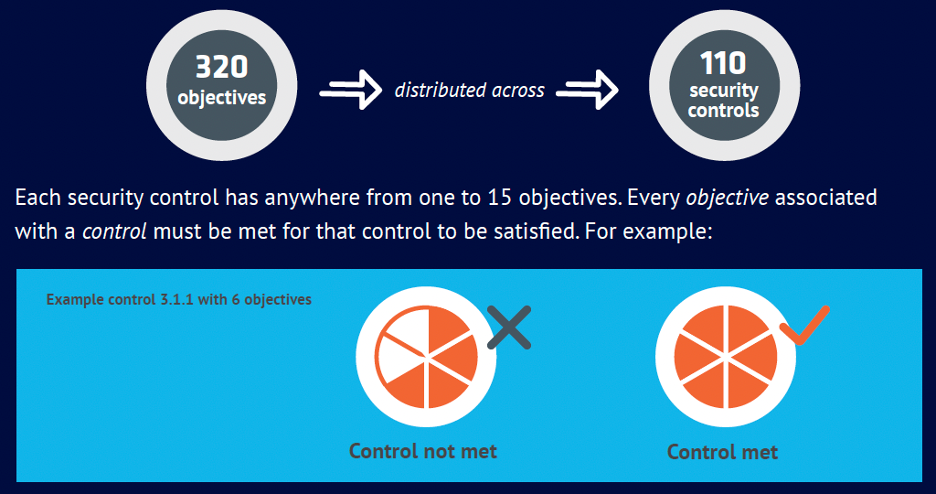
The framework outlines 110 security controls and 320 assessment objectives to evaluate compliance. Each control consists of multiple objectives, all of which must be met to satisfy the requirement
What is NIST 800-171 Compliance?
Compliance with NIST 800-171 means an organization has implemented the required 110 security controls and 320 objectives to protect CUI. For DoD contractors, NIST 800-171 compliance is essential and serves as the foundation for achieving CMMC Level 2 certification. Both standards share the same security requirements, but CMMC enforces compliance through third-party assessments rather than self-attestation.
Additionally, the Department of Justice (DoJ) has increased enforcement of NIST 800-171 through its Civil Cyber-Fraud Initiative, holding contractors accountable for false compliance claims under the False Claims Act. For instance, Georgia Tech faces legal action for allegedly misrepresenting its NIST 800-171 compliance.
How Does NIST 800-171 differ from CMMC?
NIST is a framework that provides security guidelines, while CMMC is a certification program that assesses an organization’s cybersecurity maturity. CMMC builds on NIST’s security controls to protect Controlled Unclassified Information (CUI) in the defense sector.
Who is Required to Be NIST 800-171 Compliant?
Any organization handling CUI is required to follow NIST 800-171 guidelines. This list includes:
- Prime contractors working directly with the DoD
- Subcontractors throughout the supply chain
- Universities and research institutions handling government contracts
DFARS 7012, enacted in 2017, mandates NIST 800-171 compliance for defense contractors, including subcontractors. Protecting subcontractors is important as cybercriminals frequently target them since they recognize that large defense companies typically have stronger cybersecurity measures. This makes subcontractor compliance a critical priority.
Read our Guide to CMMC, used by over 5,000 defense contractors
List of NIST 800-171 Controls
There are 14 control families in NIST 800-171 and 110 controls spread out across these families. Each family has specific requirements and guidelines that organizations must follow to ensure they are effectively protecting CUI within their information systems
- Access Control (AC): Limits access to authorized users and devices.
- Awareness and Training (AT): Ensures personnel understand cybersecurity risks and responsibilities.
- Audit and Accountability (AU): Establishes audit logs and monitoring.
- Configuration Management (CM): Manages system configurations and changes securely.
- Identification and Authentication (IA): Verifies user and device identities before granting access.
- Incident Response (IR): Detects, analyzes, and responds to security incidents.
- Maintenance (MA): Controls system maintenance and ensures security during updates.
- Media Protection (MP): Safeguards digital and non-digital media containing CUI.
- Personnel Security (PS): Screens personnel and enforces security policies.
- Physical Protection (PE): Protects physical access to CUI and IT systems.
- Risk Assessment (RA): Identifies and mitigates security risks.
- Security Assessment (CA): Conducts regular security evaluations.
- System and Communications Protection (SC): Ensures encrypted communication and secure system design.
- System and Information Integrity (SI): Detects and mitigates system vulnerabilities.
NIST 800-171 Compliance Checklist
Now is the time to take action to improve your organization’s cybersecurity posture. Here are the key steps to take to achieve NIST 800-171 compliance:
- Familiarize yourself with NIST 800-171 requirements. Familiarize yourself with the 110 controls and 320 assessment objectives. The NIST 800-171 website, provides a comprehensive list of resources to guide implementation.
- Define your compliance boundary. Identify which systems, personnel, and processes handle CUI. Creating a CUI enclave (a separate, secure environment for CUI processing) can simplify compliance.
- Adopt a platform to secure CUI. File sharing and email are primary transmission methods for CUI. Ensure your Cloud Service Provider (CSP): Meets DFARS 7012 (c)-(g), complies with FedRAMP Baseline or Equivalent standards, or higher, and uses FIPS 140-2 validated encryption.
- Develop compliance documentation. Your System Security Plan (SSP) is a mandatory document detailing how your organization meets NIST 800-171 requirements. Additional documentation, including policies and procedures, is also required.
- Conduct your NIST 800-171 self-assessment. Use NIST SP 800-171A as a guideline to assess your compliance and submit your Supplier Performance Risk System (SPRS) score. If your score is below 110, develop a Plans of Actions & Milestones (POA&Ms) to remediate gaps.
- Engage Compliance experts. If your organization lacks internal cybersecurity expertise, consider hiring third-party consultants familiar with NIST 800-171 compliance. This can save time and ensure accuracy.Engage Compliance experts. Again, get started now. Achieving full NIST 800-171 compliance typically takes 12-18 months, making it essential to start immediately to avoid disruptions in DoD contract eligibility.
Get started now. Again, get started now. Achieving full NIST 800-171 compliance typically takes 12-18 months, making it essential to start immediately to avoid disruptions in DoD contract eligibility.
How PreVeil Helps You Meet NIST 800-171 Compliance
PreVeil’s encrypted Email and Drive platform protect CUI with end-to-end encryption. In addition, it supports 102 of the 110 NIST 800-171 security controls, and 260 of the 320 assessment objectives specified in NIST 800-171A.
PreVeil also supports requirements that extend beyond NIST 800-171. PreVeil’s additional key compliance attributes include:
- Meets FedRAMP Baseline Moderate Equivalent standards
- Encrypts and stores data on FedRAMP High AWS GovCloud
- Meets DFARS 252.204-7012 (c)-(g), which stipulate requirements for cyber incident reporting
- Meets FIPS 140-2 standards for cryptographic modules used for encryption.
PreVeil is trusted by more than 1,700 small and mid-size defense contractors to meet their compliance needs faster and more affordably.
- If you have questions about how PreVeil can help your defense organization achieve compliance, contact us.
- Sign up for a free 15-minute consultation with our compliance team