When defense contractors look for a reliable source to store and share their controlled unclassified information (CUI), they will frequently turn to a cloud service provider (CSP). Cloud is a superior choice for contractors over storing on premise as cloud enables unlimited storage, access to data from anywhere, data resiliency, and freedom from managing and maintaining hardware.
The DoD considers cloud computing data centers to be extensions of contractor’s internal IT systems and so, the choice of a CSP cannot be taken lightly. Contractors must ensure that their CSP handles CUI in accordance with the regulatory requirements for FIPS validation, FedRAMP Moderate Baseline or equivalent, DFARS (c)-(g) and ITAR when necessary. If the CSP doesn’t meet these requirements, they cannot be used as part of a contractor’s CMMC 2.0 or ITAR compliance effort.
![]()
This blog is written to help contractors understand the compliance requirements that CSPs must meet for storing, sharing and emailing CUI. Our aim is to help defense contractors make informed decisions when choosing CSPs to meet their compliance needs.
Critical CSP qualifications to confirm before you commit
FIPS 140-2 Validation
FIPS 140-2 validated encryption modules are the benchmark for effective cryptographic hardware and software. They are also the encryption standard established by the US government to secure sensitive data such as CUI. Any CSP handling CUI must use FIPS 140-2 validated cryptographic modules for encryption. This standard is noted specifically in the CMMC 2.0 Self-assessment guide:
As the guide notes, CMMC 2.0 Level 2 compliance requires CSPs to protect CUI through the use of FIPS 140-1 or -2 validated modules. CSPs cannot just rely on NIST- approved algorithms. Instead, CSPs are required to complete a rigorous program where their implementation of the FIPS 140-2 algorithm is tested at each step of the way.
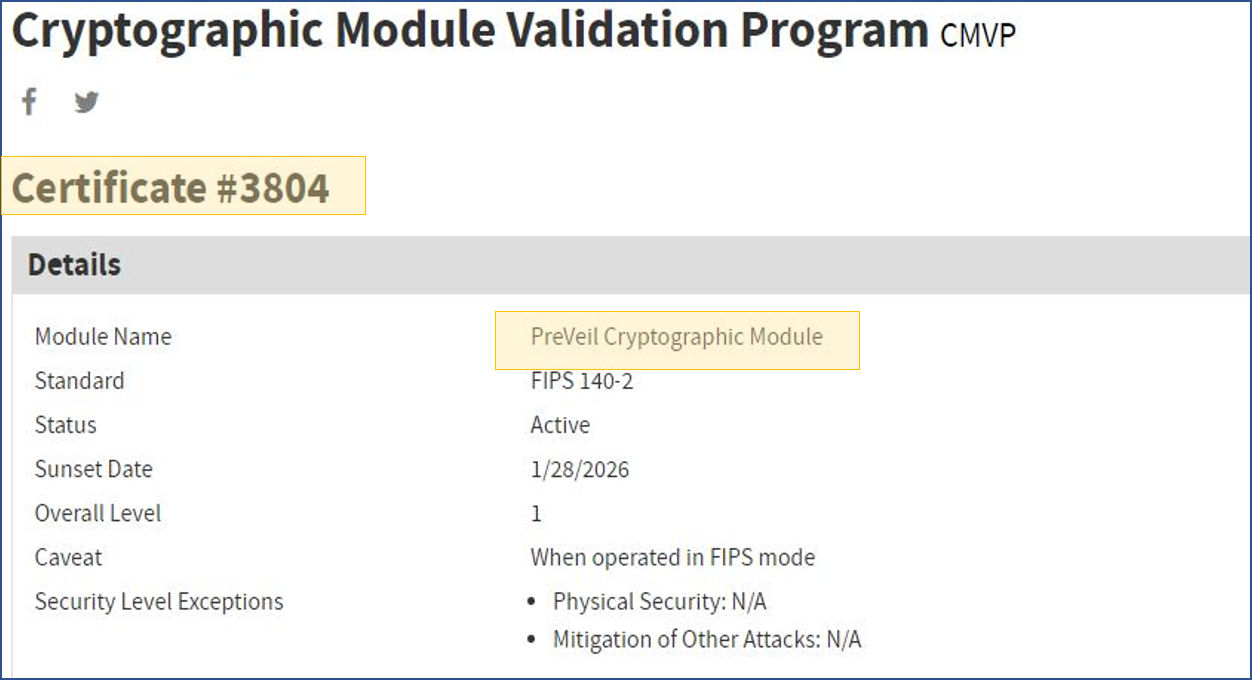
Contractors can confirm their CSP’s use of validated encryption by referencing the NIST website. For example, here’s the evidence associate with PreVeil’s NIST Cryptographic Module Validation Program (CMVP ) certificate:
Some CSPs will claim that they comply with the FIPS 140-2 standard by relying on what is termed ”FIPS inside”. That is, the provider leverages a third party-validated module that runs in FIPS mode. The challenge is that a contractor cannot confirm if its CSP’s use of FIPS continues to meet the required NIST standard. As a result, the contractor is responsible for ensuring they are operating in a compliant manner at all times and on all devices where CUI is in use. Instead, a better approach is to ask to see the CSP’s NIST CMVP validation certificate.
FedRAMP Standards
DFARS 252.204-7012(b)(2(ii)(D) notes that all CSPs storing CUI must meet FedRAMP Moderate Baseline or equivalent when processing, storing or transmitting the data. Specifically, the standard states:
On December 21, 2023, the office of the CIO, US DoD, issued a memo defining the criteria for cloud service providers to be FedRAMP Moderate baseline equivalent (summarized below):
- CSP must demonstrate 100% Compliance with the FedRAMP Moderate baseline controls with no outstanding POAMs through an assessment conducted by an independent, authorized FedRAMP third party assessment organization 3PAO. No self-attestation is permitted.
- The CSP must submit a complete Body of Evidence (BOE) for review to the Defense Industrial Base Cybersecurity Assessment Center (DIBCAC), the DoD’s highest assessment organization.
The DoD’s FedRAMP moderate equivalency requirement is more rigorous than for a FedRAMP ATO (Authorization to Operate) which typically does not require 100% compliance and allows POAM’s. It is important to underscore that an ATO is not required for DFARS and CMMC, rather it’s a compliance criterion for cloud services deployed by government agencies.
If the CSP doesn’t work directly with the Federal Government, it will need to meet the security requirements for FedRAMP Moderate equivalent, get a third-party assessment organization (3PAO) to attest to their compliance, and submit a BOE for review to DIBCAC. It is not sufficient for the CSP to simply “store” your data in a FedRAMP cloud such as AWS GovCloud or Azure Gov. The CSP itself must also attest to FedRAMP Moderate Equivalence.
For over three years, PreVeil has maintained a robust compliance program for all 325 FedRAMP Moderate controls. Compliance was validated by annual assessments conducted by independent, accredited 3PAOs and PreVeil presented its latest 3PAO assessment report and BOE to DIBCAC. A team of DIBCAC assessors conducted a thorough, multi week review of the BOE and notified the company that the DoD CIO, CMMC Program Management Office and DIBCAC concur PreVeil meets the requirements for FedRAMP equivalency.
DFARS 252-204 7012 (c)- (g) Incident reporting
The same DFARS clause that requires CSPs to meet FedRAMP Moderate Baseline or Moderate Baseline equivalent also establishes requirements for contractors to report breaches or cyberattacks to the DoD. These requirements are stipulated in DFARS 252-204 7012 (c)-(g) and state that contractors are required to provide forensic evidence to the DoD in case of an attack – evidence that the contractor will need to get from their CSP, as cloud computing data centers are seen as an extension of a contractor’s internal IT system.
In order for the CSP to provide this data, they must capture, preserve and protect images, and know the state of their systems that were affected by a cyber incident. Typically, a CSP can provide this information without needing physical access to the data center. However, in some instances physical access might be required. As such, access to the data is a requirement for CSPs meeting (c)-(g):
Most commercial cloud services are unable to attest to (c)-(g) for the very reason that they cannot enable unfettered access to their systems by DoD. For example, Microsoft will not support DFARS in its commercial O365 platform and instead only supports it in their government contractor cloud versions.
Companies can choose to augment their Commercial O365 platform with a service such as PreVeil, which supports DFARS 252-204 7012 (c)-(g).
ITAR – Data Sovereignty and Encryption requirements
Many defense contractors handling CUI also handle International Traffic in Arms Regulations (ITAR) data, which is referred to as ITAR “unclassified technical data”. Like CUI, ITAR unclassified technical data is often sensitive information about armaments and warfare. However, unlike CUI which is managed under the auspices of the DoD, ITAR data is managed by the Department of State, which has placed unique controls over ITAR’s transmission and storage.
The highest hurdle for CSPs to meet is ensuring that ITAR technical data is never inadvertently distributed to foreign persons or foreign nations. In order to ensure this, a CSP managing unclassified technical data must:
- Store all technical data on servers located within the US on a sovereign cloud
- Ensure the cloud is solely managed by US persons in US locations
- Ensure the data never leaves the US
For CSPs, meeting these requirements is a significant and expensive challenge.
The other option available to CSPs managing ITAR data is to use end-to-end encryption to secure all data. In March of 2020 the Department of State adopted the ITAR Carve out for Encrypted Technical Data, which established that defense companies can share unclassified ITAR technical data so long as:
- The data is properly secured with end-to-end encryption
- The data is secured with end-to-end encryption using FIPS 140-2 validated algorithms
- CSPs can’t access the decryption keys
- The data is unclassified
- Data is not intentionally sent to a person in or stored in restricted countries
- Data is not intentionally sent from a restricted country
The Department of State defines end-to-end encrypted data as:
The data is never decrypted in transit or when stored by the CSP. As part of this definition, the State Department also requires that the ‘means of decryption are not provided to any third party ’.
PreVeil’s Email and Drive platform utilize end-to-end encryption to ensure data security and confidentiality. With PreVeil, data is encrypted on the sender’s device and is only ever decrypted on the recipient’s device. No one but the sender and recipient have the decryption keys – not even PreVeil. As a result, PreVeil can significantly aid defense contractors seeking ITAR compliance.
Multiple PreVeil Customers to achieve 110/110 CMMC, NIST 800-171 Scores in DoD Assessments
Contractors looking for a simple, secure and compliant platform for storing and sharing CUI should consider PreVeil. PreVeil uses FIPS 140-2 validated cryptographic modules for encryption, is certified as FedRAMP Moderate Baseline equivalent, meets DFARS 252.204-7012 (c)-g, and uses end-to-end encryption to secure all data.
PreVeil’s internal compliance credentials and encrypted email, file sharing products have enabled a rapidly growing number of customers to achieve 110/110 Scores in NIST 800-171 and CMMC Joint Surveillance Assessments conducted by DIBCAC and CMMC 3PAOs. PreVeil utilizes its compliance expertise to provide detailed CMMC and NIST 800-171 documentation to our customers. Our documentation streamlines the process and reduces the cost and time required by our customers to achieve compliance. These successful assessments are the ultimate validation the PreVeil solution’s benefits of compliance assurance, best in class security and low cost for defense contractors.
Conclusion
Today, many CSPs are promising contractors they can help them meet the mandates of CMMC , NIST 800-171, DFARS 7012, FedRAMP and ITAR, and achieve compliance. The challenge is to ensure that the CSP you are considering working with actually meets the mandates required by the DoD or Department of State for protecting CUI or ITAR data. Do your research and ask the CSP you are considering contracting with for DoD certification and/or documentation that they meet the critical standards described above and if they’ve helped contractors go through DoD assessments. Otherwise, your organization runs the risk of wasting time and money, and introducing compliance deficiencies and complexities—as opposed to improving your cybersecurity levels and increasing your competitiveness in the Defense Industrial Base.
![]()
If you have questions about how PreVeil can help your defense organization achieve compliance, contact us.