Tips for Digital Privacy and Security
You might think business email compromise (BEC) attacks are only a concern for large financial institutions, but that’s not true. Online, everyone is a potential victim. In June 2021 a San Francisco-based charity, Treasure Island, lost $625,000 after hackers infiltrated the organization’s bookkeeper’s email. In a separate incident in March 2021, three hackers conspired to steal over $1.1 million through a series of BEC attacks in which they posed as victims’ clients in order to intercept payments.

End-to-end encrypted email is the solution. End-to-end encryption scrambles your data, so only you and your intended communication partner can access the message. In a digital landscape full of hackers, this is essential to maintain your privacy and info security.
How Email Encryption Works
Protecting your sensitive information online is an important part of participating in a digital world. End-to-end encryption scrambles your messages at all times other than when you and your intended recipient are accessing them.
While transport security is often confused with data encryption, they’re not the same thing. You can encrypt the transport layer, or the message itself, or both. For true security, encrypt both.
Transport Layer Security (TLS) encrypts the message while it is in transit. That is, your message is secured while it is traveling from your inbox to your recipient’s. This prevents a hacker from swooping in while the message is in transit and intercepting it. Major email providers, including Gmail, Yahoo, and AolMail, have made this level of protection standard.
Protecting emails during transit is not enough, however. TLS encryption still leaves your messages naked on a server. Servers are common targets of hackers. If they can get in, they have access to a treasure trove of user data.
End-to-end encryption closes that security gap. End-to-end encryption encrypts your messages at all times – even when stored on the server. This means your data is safe even if hackers breach the server.
No matter how well a server is defended, server breaches are inevitable – there are bad actors the world over working on breaching those defenses every minute of every day. End-to-end encrypted email protects you even when the bad guys get in. They’ll never be able to see your data.
Types of Email Encryption
Email encryption has evolved over time. First came PGP encryption, then S/Mime encryption, and finally a combination of symmetric encryption and asymmetric encryption.
Pretty Good Privacy (PGP) encryption was the first widely used method of message encryption. It relied on asymmetric encryption, in which a public key encrypts messages and a unique private key decrypts messages. Only the individual message recipient has access to their specific private key.
Here’s how PGP works:
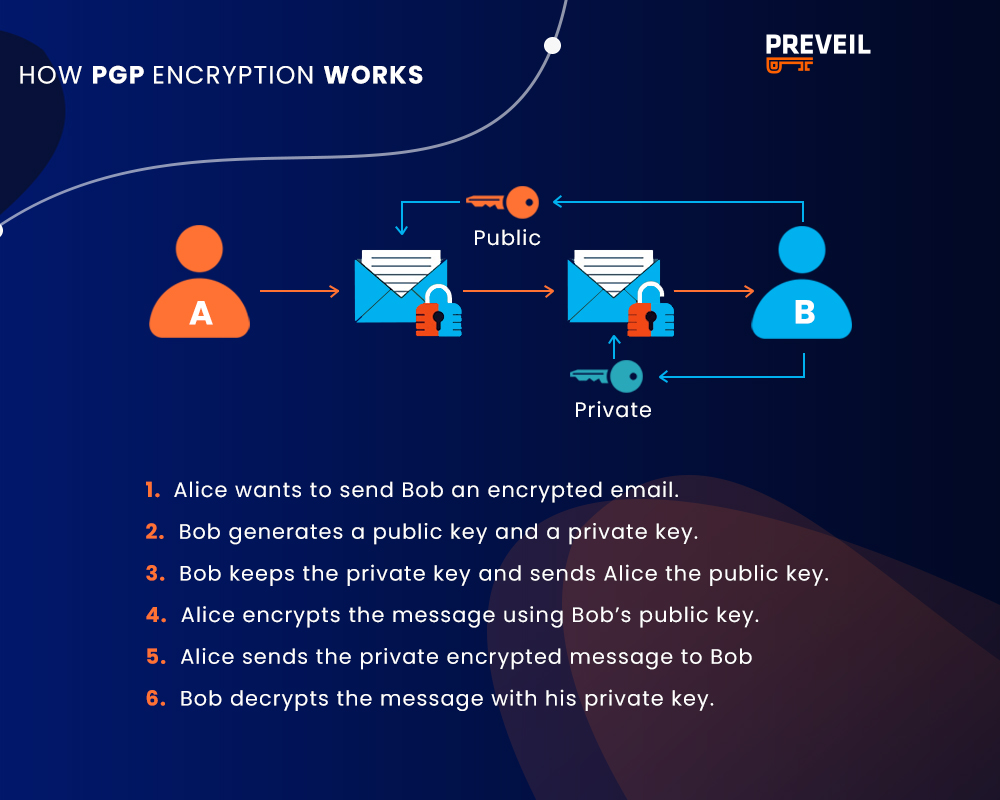
There are a few major problems with PGP encryption, including inefficiency and the possibility of completely losing access to your own data.
Problems with PGP encryption:
- If you lose your private key, there is no way to recreate it – you’re out of luck. There’s no way of accessing your data.
- End users are responsible for distributing their own p ublic keys to the people they want to talk to. There’s no central way to do this, making PGP an inefficient system that scales poorly.
- If you lose your device, then you have to go through the process of exchanging your public key with all your correspondences all over again. Moreover, any email that was secured with your original key cannot be decrypted. In this case, too, you will lose access to your own data.
As you can see, these are some serious issues. PGP’s deficits led to the creation of S/MIME.
S/MIME, used by the Department of Defense (DoD) among others, relies instead on digital certificates for encryption. Secure/Multipurpose Internet Mail Extensions (S/MIME) also uses asymmetric encryption to protect emails. With S/MIME either a central authority, for example the DoD, or an individual can manage the private key. This improves usability for individuals in an organization.
S/MIME is the main way that the DoD and Microsoft encrypt emails. However, S/MIME certificates periodically expire and must be updated. This creates a lot of management overhead, making S/MIME inefficient. Organizations with small IT teams don’t have the resources to accommodate this inefficiency.
Further, S/MIME is not available for web-based email clients, like Gmail, and cannot be accessed through a web portal. This worsens usability.
S/MIME often protects against account lockout by storing copies of private keys on the server. If that happens, criminals can get copies of users’ private keys by attacking the server. S/MIME is thus not always as secure as PGP.
The shortcomings of S/MIME and PGP inspired the creation of a new, better form of encryption: combined symmetric and asymmetric encryption. End-to-end encrypted email providers, like PreVeil, rely on this combination of strategies to secure emails in an effective, user-friendly, and scalable way. End-to-end encryption keeps your data safe at all times and, unlike PGP, takes care of key management for you.
PreVeil manages the public keys, so you don’t have to. PreVeil uses symmetric keys to encrypt and decrypt information. Symmetric keys are much faster at performing encryption and decryption operations than asymmetric keys, but by themselves aren’t very scalable. PreVeil solves this problem by adding on asymmetric keys to manage identity and access to information.
Asymmetric keys have a public component known as a public key, which is shared to everyone in the PreVeil system, and a private component (a private key), which remains solely on user devices. Asymmetric cryptography was designed to be scalable, since each new user only needs to share a single public key in order to share their identity and have information be encrypted for them. By combining asymmetric and symmetric encryption, PreVeil provides all the advantages of S/MIME security without a single point of failure and without any management overhead.
It’s quick. It’s secure. It’s easy.
How to Encrypt Emails
As you can see, not all encryption is created equal. When choosing an encrypted email provider, look for a protocol that relies on end to end encryption while also being secure, easy to manage, and integrates with your existing email platform. PreVeil satisfies all the requirements for a secure, user-friendly encrypted email provider. Here’s how to get started with PreVeil Email in mere minutes.
- Download and deploy PreVeil. Click download. Open the file in your downloads folder, while leaving your browser open. Accept the license agreement and click ‘install.’
- Create your account. Click ‘create account.’ Enter your email address (this will be your PreVeil ID), and then click ‘Send Verification Email.’ Access your email account to view the verification code. It may be located in your spam/junk folder. Copy the verification code to the browser window and click ‘Verify.’
- Set up the Gmail or Outlook plugin. If you want to use PreVeil Email with Gmail or Outlook, click ‘add PreVeil to Outlook’ or ‘add PreVeil to Gmail.’
- Backup your keys. Click on ‘Settings’ then ‘Recovery Code.’ Optionally enter a password then click ‘Create Recovery File.’ A PDF will be downloaded to your Downloads folder. You can scan the code in the future to recover your account if you need to. This will work one time only (after which you’ll need to download a new code).
- Start using PreVeil Email!
As noted above, PreVeil can be used in conjunction with your existing Outlook, Gmail, and Apple Mail accounts by downloading the appropriate plugin. In this case, PreVeil adds an encrypted inbox to your existing account, allowing you to continue using your existing email address. Emails sent to PreVeil users will automatically be encrypted, while non PreVeil recipients will receive an invitation to quickly create a free account.
PreVeil also offers a mobile app from the iOS or Android store.
This combination of security and usability have made PreVeil PC Magazine’s Editors Choice for four years in a row. PC Magazine recommends PreVeil as “end-to-end encrypted secure cloud storage along with secure email that’s tough enough for business but extremely easy to use, all while keeping your existing email address.”
Benefits of Email Encryption
End-to-end encryption for email is more important than ever in today’s increasingly virtual world. End-to-end encrypted emails protect against eavesdropping, ensuring that your privacy is maintained online. They protect against data interception, ensuring that sensitive information isn’t leaked to competitors or bad actors. Finally, end-to-end encrypted emails protect against unauthorized access, ensuring that only the individuals you intend to communicate with can read your messages.
PreVeil achieves this goal through the use of end-to-end encryption to protect your emails in four main ways. PreVeil protects against server breachers, password theft, admin attacks, and phishing/spoofing attacks.
- Protects Against Server Breaches: PreVeil understands that servers are favorite targets of hackers. No matter how tall you build the wall around a server, it’s impossible to guarantee that it’s hack-proof. Instead, PreVeil uses end-to-end encryption to ensure that your data is safe even in the event of a server breach.
- Protects Against Password Theft: PreVeil understands that passwords are inherently vulnerable. By granting access to your accounts via a public-private key pair, PreVeil eliminates passwords. This not only improves the security of your account, but also user friendliness.
- Protects Against Admin Attacks: PreVeil uses approval groups to eliminate administrators as single points of failure. In the traditional model, a compromised administrator can bring down your whole system. With approval groups, no individual has the power to access the accounts of others.
- Protects Against Phishing and Spoofing: Finally, PreVeil uses trusted communities to protect against phishing/spoofing attacks in the workplace. With trusted communities, encryption verifies the identity of all individuals within the community. You can send emails freely, knowing that the person you’re communicating with really is who they claim to be.
PreVeil’s rigorous security standards support compliance with data protection regulations across industries, including CMMC, ITAR, HIPAA, and more. Over 2,500 contractors in the defense industrial base (DIB) depend on PreVeil to satisfy the industry’s stringent cybersecurity requirements. These military-grade protections come at savings of up to 60% over alternatives.
Next Steps
Encrypted email is a key part of securing data online. All encryption is not created the same – look for an end-to-end encrypted email provider, like PreVeil, that uses a combination of asymmetric and symmetric encryption to protect your communications in a secure, user-friendly way.
If you need help or have questions about encrypted email, please don’t hesitate to reach out and schedule a free 15-minute consultation with PreVeil’s support team.