The Leading Solution for CMMC Compliance
Trusted by over 1,800 defense contractors & C3PAOs.
Proven. Easy to use. Save 75% vs GCC High.

CMMC is Here: Are You Ready?
Failure to implement CMMC/ DFARS controls could violate current contract requirements & jeopardize future DoD opportunities
Join thousands of defense contractors who’ve used PreVeil to meet CMMC controls & cut costs by 75%
Achieve CMMC with PreVeil
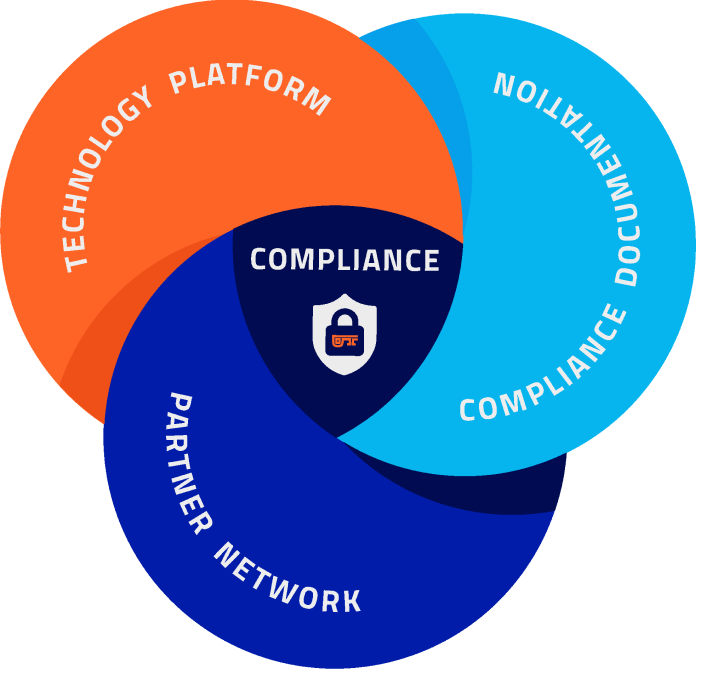
PreVeil’s Comprehensive CMMC Solution
PreVeil’s platform and documentation provide guidance to address all 110 CMMC/NIST controls
Encrypted File Sharing + Email
Protects CUI without overhauling existing systems. Integrate with O365, GSuite, Outlook, and Exchange.

CMMC Compliance Accelerator
Detailed, Pre-filled, customizable documentation with videos and tutorials to simplify achieving compliance.

Network of Trusted Partners
Access our network of C3PAO and consultants to refine your documentation & streamline your assessment.

A Proven Solution for CMMC Compliance
Defense contractors & C3PAOs have used PreVeil to achieve CMMC compliance with perfect 110 scores






Our Proven Track Record Includes:
110/110 CMMC Scores
PreVeil customers have achieved perfect 110 scores on CMMC assessments.
FedRAMP Moderate Requirements
Equivalent security to protect Controlled Unclassified Information (CUI).
FIPS 140-2 Validated Encryption
Cryptography certified to meet CMMC and ITAR standards.
DFARS 7012 (c-g) Requirements
Compliance for Cyber Incident Reporting and CUI protection.
Save $200,000 vs GCC High
When it comes to rapid compliance at a low cost, PreVeil is undoubtedly the right decision. We got it done on time and on budget, saving $200,000 compared to GCC High
Defense contractor that achieved CMMC compliance with a 110/110 score
Unrivaled Security to Meet Compliance
End-to-End Encryption
Data is encrypted from the sender’s device to the recipient, blocking hackers even if servers are breached.
Zero Trust Architecture
Protects against insider and admin threats, plus built-in ransomware protection ensures quick recovery.
The PreVeil Platform
PreVeil simplifies compliance while offering industry-leading security and ease of use. Our platform integrates seamlessly with your existing email and file sharing systems to protect CUI and meet compliance requirements.
PreVeil Drive
Securely encrypt, store, and share files, directly from Windows Explorer, Mac Finder and on browsers.
PreVeil Email
Send and receive end-to-end encrypted emails using your existing email address from Outlook, Gmail, Apple Mail, Browsers and PreVeil’s Mobile app
Share with 3rd Parties for Free
Subcontractors and other 3rd parties can create PreVeil Express accounts for free, so you don’t need to manage and pay for costly Guest Accounts.
Encrypted storage for email and files, on a sovereign FedRAMP High Cloud.
Amazon GovCloud Storage
Discover how PreVeil can transform your compliance journey.
Who We Serve Best
Tailored Solutions for Every Sector:
Small and Medium Businesses
Minimize costs with the PreVeil Pass.
Large Enterprises with Defense Subsidiaries
Streamline compliance for users handling CUI by creating an Enclave.
International Companies
Navigate conflicting regulations with seamless integration.
Universities Conducting Defense Research
Maintain collaboration while securing DoD research data.
Why Choose PreVeil vs Microsoft GCC High
Two Solutions, Two Approaches
PreVeil provides exceptional security and compliance in a simple, cost-effective solution—ideal for small and mid-sized organizations.
Key Differences at a Glance
| Feature | Microsoft GCC High | PreVeil |
| Best For | Large enterprises with dedicated IT & compliance teams | Organizations of all sizes, particularly SMBs seeking simplicity and affordability |
| Deployment | Requires disruptive and costly migrations of IT systems | Seamlessly integrates with your existing IT setup |
| Cost | High, with expensive license fees and documentation challenges | Affordable, with pre-filled compliance documentation, saving tens of thousands |
| Supplier Collaboration | Requires expensive guest licenses | Free, encrypted accounts for 3rd parties |
| Ease of Use | Complex, requiring significant IT resources | Easy to deploy and manage, even for SMBs |
Affordable Compliance for SMBs
PreVeil Pass
Save tens of thousands in compliance costs while meeting CMMC requirements, preparing documentation, and boosting your SPRS score—all for just $4,999/year.
What’s Included:
3 User Licenses: Secure communication and file sharing.
Admin License: Simplified compliance management tools.
Compliance Accelerator Documentation: Prefilled, customizable documentation and videos.
Personalized Onboarding: Live setup assistance in under an hour.
Hear from Our Customers

Small Defense Contractor
“When it comes to speed to compliance & cost, PreVeil is undoubtedly the right decision. We got it done on time & on budget, saving $200,000 vs GCC High”

5 Years in a Row
Best Encrypted Email & File Sharing
With PreVeil, you get … end-to-end encrypted secure cloud storage along with secure email that’s tough enough for business but extremely easy to use, all while keeping your existing email address.
Neil Rubenking, PC Magazine



