In a recent customer discussion, a CISO shared his concern with me regarding his company’s data. He worried that confidential data that had been shared with their suppliers would be leaked. He was worried that unsecured points in the supply chain could unveil this information to competitors or to the market before his company was ready for its release.
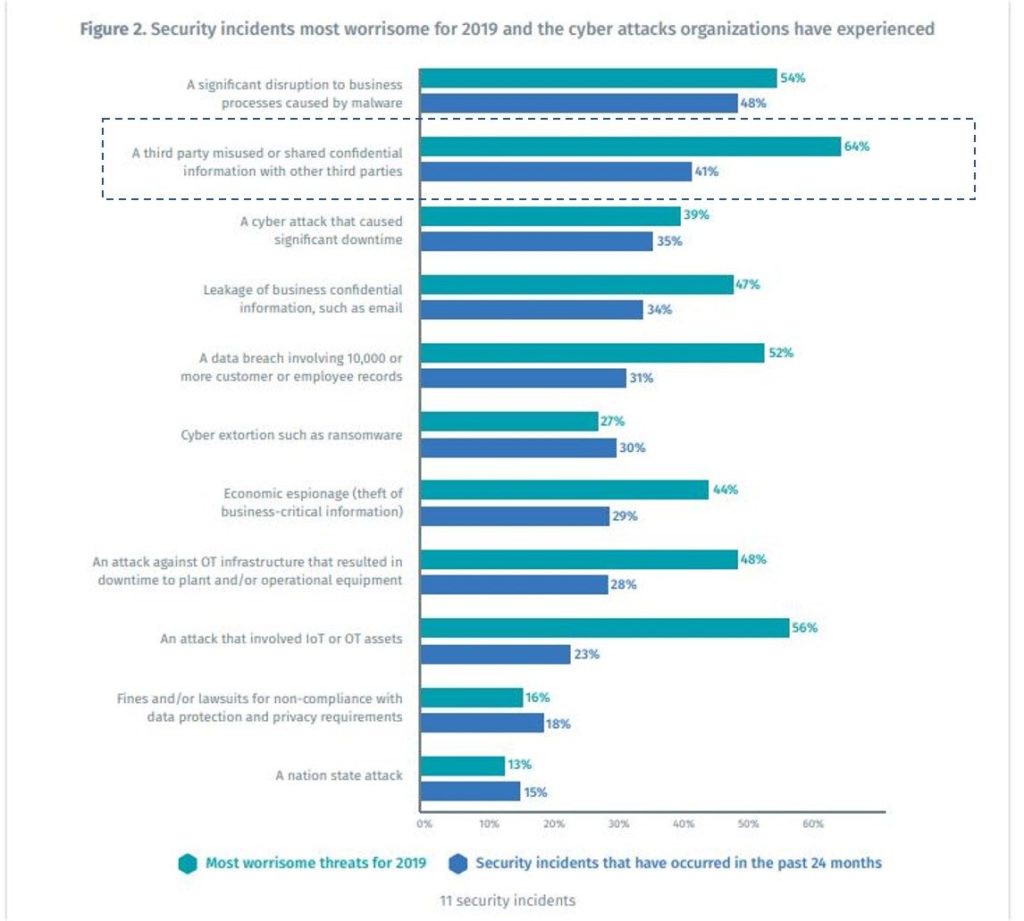
Ponemon Institute: Measuring and Managing the Cyber Risks to Business Operations
As shown in the Tenable/ Ponemon Institute graph above, third party misuse of company data is one of the most worrisome threats for organizations.
Clearly, problems like those expressed by this CISO are not as unique as I would hope. So, what can enterprises do when faced with information security threats up and down the supply chain? Direct IT control is not possible and no network perimeter exists. So how can the enterprise keep out bad actors?
Regulation is Increasing in the Supply Chain
There is a good quote I found in a 2018 Mitre publication: Deliver Uncompromised: A Strategy for Supply Chain Security and Resilience in Response to the Changing Character of War.
“For mission owners, the primary goal of DoD must be to deliver war fighting capabilities to Operating Forces without their critical information and/or technology being wittingly or unwittingly lost, stolen, denied, degraded or inappropriately given away or sold.” William Stephens, Director of Counterintelligence, DSS.
This just highlights the increased scrutiny the DoD’s placing on the supply chain’s security.
Mitre 2018 study: Deliver Uncompromised
Among the companies in our customer base, we see the regulatory requirements imposed at the top of the chain flowing down to suppliers. For example, our Aerospace and Defense industry customers and partners tell us that retaining business and winning new contracts will require compliance with Defense Federal Acquisition Regulations Supplement (DFARS) for sensitive program data.
The Department of Defense made DFARS Compliance required by any company that generates DoD-related revenue to protect its sensitive data that lies within its supply chain from being compromised
For DoD-related procurement, enforcement of NIST 800-171 guidance under DFARS is ramping up as well. Prime contractors insist that all levels of their supply chain, including companies of any size, demonstrate proper IT governance prior to winning future awards.
Less Regulated Companies also at Risk
Supply chain cybersecurity risks are just as real for SMBs. Small and mid-size business (SMB) make up a large portion of today’s supply chains. These chains provide critical goods and services to all industries. But this long distribution tail means critical company information can be lost or stolen.
I came across an interesting statistic from Crowdstrike. According to the article, 70 percent of cyberattacks target small businesses. According to the article:
Small businesses are in possession of many assets that are of great interest to adversaries, including money, intellectual property (IP), customer data and access. In fact, access may be a primary driver because an SMB can be used as a vector to attack a larger parent organization or the supply chain of a larger target.
Yet we know that SMBs are among those least likely to have a robust security policy to protect them from cyberattacks. Instead, the current approach for protecting SMBs on the supply chain is largely based on a hope the company won’t be attacked.
The Solution
Protecting the supply chain starts by presuming all systems will be successfully attacked. We need to consider that it’s a matter of “when, not if” the attack occurs. This type of thinking though requires an entirely new approach to message and data security.
Deploying end to end encryption to secure message and file sharing provides this new way of thinking. End-to-end encryption is a powerful way to ensure that messages and data are never compromised, even if successfully attacked. And, it is the solution that can protect systems even during or after a successful attack.
End-to-end encryption enables trusted communications, meaning that messages and data are always safe and encrypted — only the sender and desired recipients can see it. Unlike most other server-based email and file sharing approaches, there are never any decryption keys stored in the cloud or on servers that can be exploited to reveal critical messages or data.
With end-to-end encryption, admins don’t have decryption keys. So, data remains secure even if servers are breached.
We know that privileged admin accounts can represent a big challenge to the supply chain. They can be exploited to provide attackers unlimited access to company information. Eliminating reliance on single admin account is also necessary to make a solution immune from admin compromises.
Additionally, secure communications up and down the supply chain means only cryptographically designated people can participate in sending and receiving messages and sharing corporate data. Attackers cannot participate or phish within the community.
Final Thoughts
I am suggesting that IT security practitioners, CIO, CISO, and others consider a new approach to addressing the pervasive set of security and privacy problems that we have all inherited from yesterday’s email and file sharing technologies. This is particularly urgent in a supply chain scenario, where there is no network perimeter, no direct IT control, and no audit trail across the various companies.
Facebook Messenger, WhatsApp and others have already converted to an end to end encryption-based approach, and this is a trend worthy of note. In future, enterprises, their users, and supply chain partners will all have a basic expectation for security, privacy and compliance, even when successful cyberattacks occur. End to end encryption technology can deliver this additional security without disrupting the velocity that today’s businesses rely on to win.