The Cybersecurity Maturity Model Certification (CMMC) is a framework introduced by the Department of Defense (DoD) in 2019 to ensure defense contractors comply with cybersecurity requirements outlined in NIST SP 800-171. Its primary goal is to protect sensitive information, such as Federal Contract Information (FCI) and Controlled Unclassified Information (CUI), while strengthening the overall security of the defense supply chain.
This blog explains the basic requirements of CMMC, latest timeline, projected costs of compliance, and tips on how to get started on CMMC compliance.
Table of contents
What is CMMC Compliance?
CMMC Compliance was introduced by the Department of Defense (DoD) to address widespread gaps in compliance and enforcement of the existing NIST SP 800-171 framework. While CMMC compliance doesn’t introduce new cybersecurity requirements for protecting FCI and CUI, it strengthens enforcement of the security measures already in place.
Previously, defense contractors were allowed to self-assess their compliance with DoD security requirements. Under CMMC, however, most contractors will need to undergo independent third-party assessments to verify compliance. These assessments will be conducted by CMMC Third Party Assessment Organizations (C3PAOs) that are trained and certified by the Cyber AB, CMMC’s official accreditation body.
Who Needs CMMC Certification?
Organizations that handle FCI or CUI must achieve CMMC certification at the level specified in their contract. This requirement applies not only to large, Prime defense contractors but also to subcontractors and smaller organizations further down the Defense Industrial Base (DIB) supply chain. Cybercriminals often target these smaller entities, viewing them as less secure entry points to sensitive data. By raising cybersecurity standards across the entire supply chain, the DoD aims to mitigate these vulnerabilities—a core objective of the CMMC program.
CMMC Levels and Their Compliance Requirements
CMMC has three levels of compliance, determined by the type of information your organization handles. To work on defense contracts, your organization must comply with the CMMC level specified in your contract and undergo the appropriate assessments, as shown in the figure below.
Security and assessment requirements—based on CMMC Level
Source: DoD Chief Information Officer website
- Level 1 applies to organizations handling Federal Contract Information (FCI) only. Compliance requires meeting the basic safeguarding requirements outlined in FAR 52.204-21. Organizations at this level must perform annual self-assessments to verify compliance.
- Level 2 is designed for organizations that handle Controlled Unclassified Information (CUI). Compliance at this level involves meeting the 110 security controls specified in NIST SP 800-171. Most organizations at this level will need to undergo third-party assessments every three years. These assessments are conducted by accredited CMMC Third Party Assessment Organizations (C3PAOs), who evaluate compliance with NIST SP 800-171 controls..
- Level 3 applies to organizations working with CUI and facing Advanced Persistent Threats (APTs)—sophisticated, state-sponsored attacks targeting critical defense programs. To achieve Level 3, organizations must comply with both the 110 NIST SP 800-171 security controls and an additional 24 enhanced security controls from NIST SP 800-172. Triennial assessments at this level are conducted by the Defense Industrial Base Cybersecurity Assessment Center (DIBCAC), the DoD’s ultimate authority on compliance.
When Will CMMC Compliance Be Required?
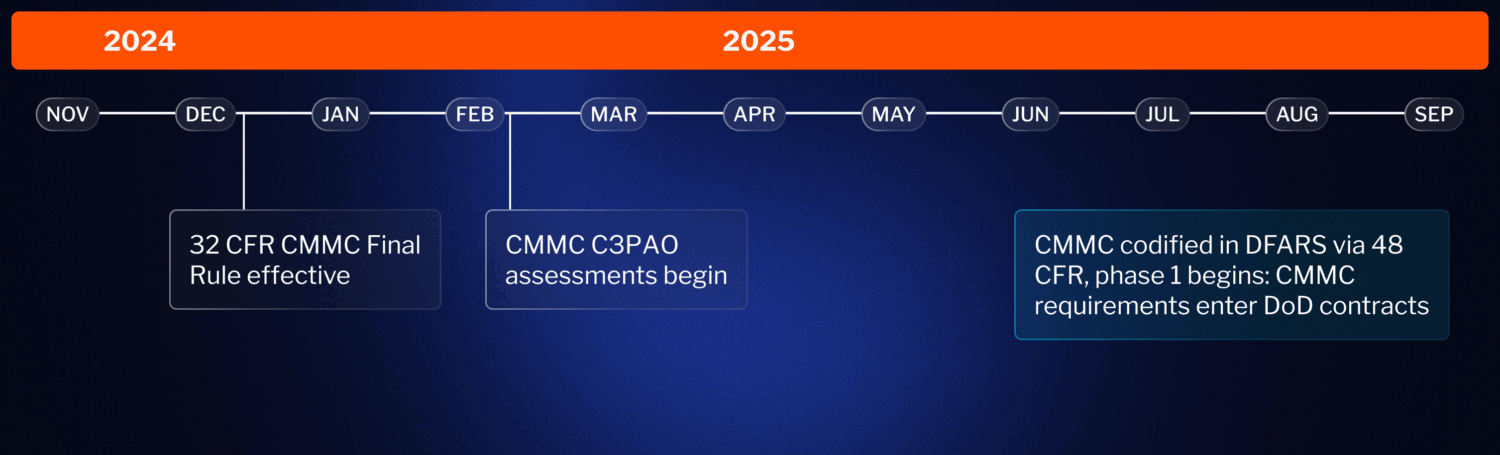
The CMMC Final Rule (CFR 32) became effective on Dec 16, 2024 and CMMC assessments have begun. It will enter contracts by Mid-2025. See our CMMC timeline blog for more details.
It is important to understand that even though CMMC will be phased in over time, it does not necessarily follow that you have more time to achieve CMMC certification. Your organization, for example, could be far down the supply chain from a contractor subject to CMMC in Phase 1, in which case that contractor must flow down CMMC requirements to your organization at that time.
As leading cyber lawyer Robert Metzger said during PreVeil’s CMMC Summit:
The problem for most contractors is that you won’t know in advance when the compliance requirement will come to you or when your Prime will ask you to show you are ready for a certification assessment. Most organizations find that it takes 6-18 months to know that you are ready to pass an assessment. So you need to get started now.
CMMC Compliance Costs
The costs associated with achieving CMMC Level 2 certification can vary widely depending on several factors. These include your organization’s current cybersecurity maturity, the scope of your Controlled Unclassified Information (CUI) enclave, the number of employees handling CUI, the extent of internal preparation for the C3PAO assessment, and the need for external expertise to meet certification requirements.
Want to know how much CMMC will cost your organization?
Check out our CMMC Cost Calculator
The DoD estimates that the cost of CMMC Level 2 assessments and required affirmations of compliance will exceed $100,000, excluding any additional technology investments needed to meet requirements. The table below provides a breakdown of cost estimates for small defense contractors (fewer than 500 employees or less than $7.5 million in annual revenue):
DoD CMMC Level 2 Certification and Cost Estimates for small defense contractors (with < 500 employees or revenue < $7.5 million)
Source: Proposed Rule: Cybersecurity Maturity Model Certification Program
These costs include time and resources from both in-house IT specialists and external service providers, such as Registered Practitioners (RPs) and C3PAOs, who assist in achieving CMMC Level 2 compliance.
However, it’s important to note that these estimates begin at the C3PAO assessment phase and exclude any costs incurred beforehand. Since defense contractors have been required to comply with NIST 800-171 standards—on which CMMC Level 2 is based—since 2017, the DoD does not consider NIST 800-171-related technologies or documentation as new expenses.
The good news is that there are technology solutions available that can significantly reduce the time and cost of achieving compliance. PreVeil’s blog, 6 Ways to Save Money on CMMC, offers insights into the costs involved and practical strategies to save money at each step of the process.
How to Become CMMC Compliant: 3 Steps to Get Started
If you’re just starting your CMMC Level 2 compliance journey, you should focus on meeting the 110 controls in NIST 800-171. PreVeil offers a three-step roadmap to NIST 800-171 compliance and CMMC Level 2 certification.
1. Adopt a platform that securely stores, processes and transmits CUI.
You’ll need to choose an email and file sharing platform that complies with DFARS 7012. Know that common commercial email solutions like Gmail and Microsoft O365 are not compliant & the responsibility for choosing a compliant platform rests squarely on the shoulders of defense contractors; Ask for documented evidence and ask for customers who have achieved CMMC compliance.
Dozens of PreVeil customers have achieved CMMC compliance- validated by a perfect 110 score on their C3PAO or DoD assessment. PreVeil is used by over 1,800 defense contractors and provides a comprehensive solution to simplify CMMC compliance. Through a combination of inherited and shared controls, PreVeil supports over 90% of the NIST SP 800-171 security controls (102 of the 110).
2. Use prepared documentation to show compliance and save time and money.
Defense contractors have to do more than implement technology and policies to comply with NIST SP 800-171. They also need detailed, evidence-based documentation to prove it. This can be a daunting, time-consuming, and costly task.
PreVeil offers its customers a Compliance Accelerator documentation package that gives them a huge head start. It includes a pre-filled System Security Plan (SSP) with detailed language that explains how a customer will be able to meet each of the NIST SP 800-171 controls and objectives that PreVeil supports; policy documents; POA&M templates and more. Here’s what Paul Miller from Virtra said:
I would say the Preveil supporting documentation halved our time that we spent on the SSP. The pre-filled documents gave us that starting place to make sure we addressed everything in each control.
3. Identify certified consultants that are familiar with your technology
It’s understandable that many organizations lack the internal security expertise to conduct their NIST 800-171 self-assessment accurately and cost effectively. If you get stuck and need help, outside partners can save you time and money.
To facilitate connections to the specialized help many small to midsize businesses need, PreVeil has built a partner network of C3PAOs, Registered Practitioners, MSPs and other consultants—all with expert knowledge of DFARS, NIST, CMMC and PreVeil.
Now is the time to get started on CMMC compliance. Informed estimates from C3PAOs who have done this work are that it takes typical small to midsize organizations around 12 months to meet CMMC Level 2 requirements. That time frame exceeds estimates of how long it will be before CMMC requirements begin to appear in DoD contracts.
To Learn More about CMMC Compliance
PreVeil is trusted by more than 1,800 small and midsize defense contractors. Learn more about how PreVeil can help you achieve CMMC Level 2 certification faster and more affordably: