The Proven CMMC Solution for Defense Contractors
Trusted by over 1,700 contractors.
Deploys in Hours. Easy to use. Save 75% vs GCC High.







Compliance Requirements for Defense Contractors
Small-to-medium aerospace contractors must meet stringent compliance requirements to win & maintain DoD contracts.
PreVeil’s comprehensive solution helps you meet these requirements while ensuring unmatched security, affordability and simplicity.
DFARS 7012
Protect CUI with encrypted email & file sharing, plus support for 102 out of 110 NIST 800-171 controls
CMMC
Proven CMMC solution includes technology platform, pre-filled documentation, & partner network
DFARS 7020 & SPRS
Rapidly increase your SPRS score by 100+ points with our comprehensive solution
ITAR
Share ITAR data without it becoming an export since PreVeil meets ITAR’s data security requirements
FedRAMP & FIPS
PreVeil meets FedRAMP Moderate Baseline Equivalent & uses FIPS 140-2 validated encryption modules
Comprehensive Compliance Solution
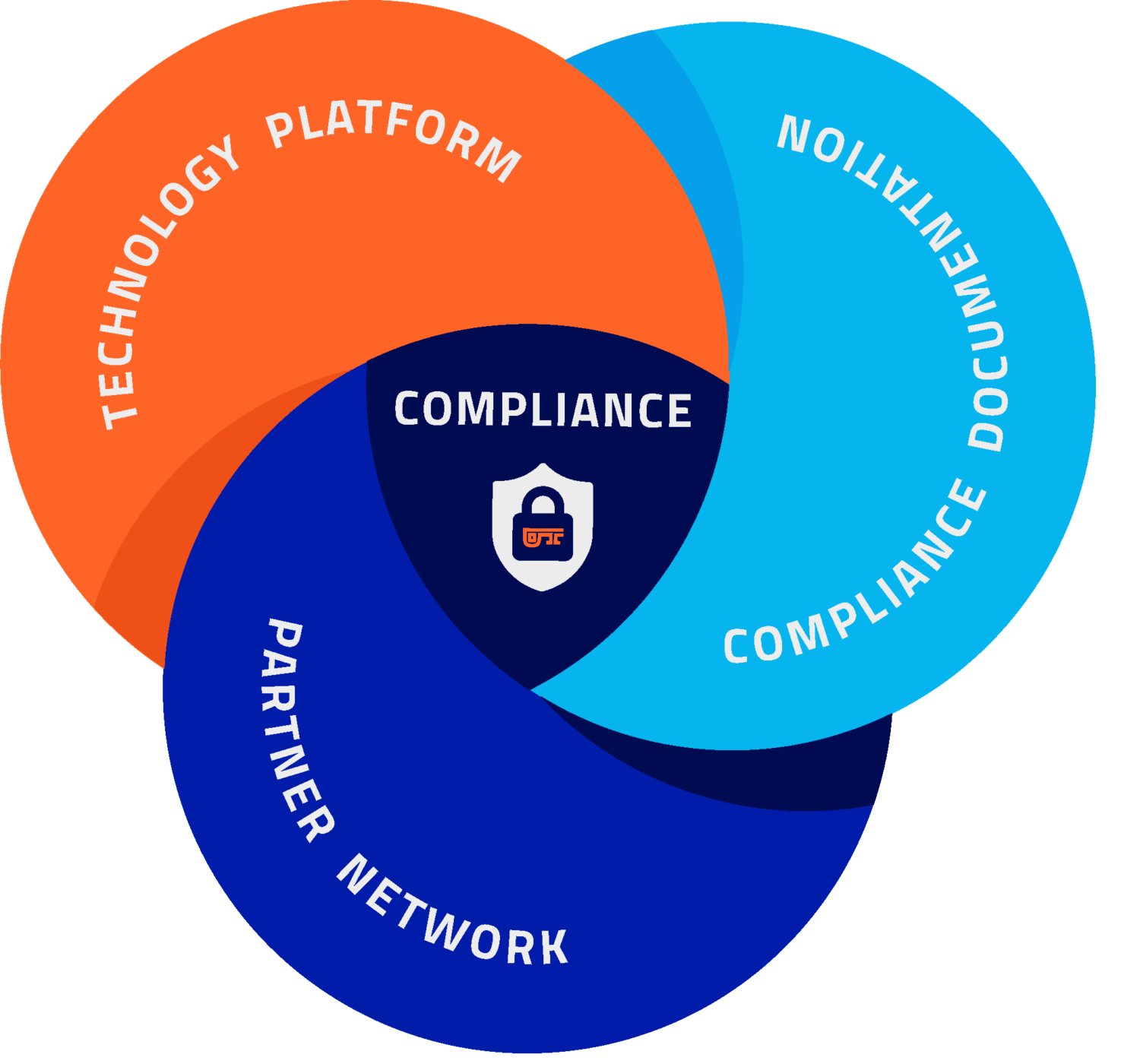
Technology Platform
Email & Drive file collaboration protect CUI with end-to-end encryption. Meets FedRAMP, FIPS 140-2, and DFARS 7012 c-g.
Compliance Accelerator
Pre-filled CMMC documentation (Standard Operating Procedure, System Security Plan, etc), assessor-validated videos, and 1×1 support from our compliance experts.
Partner Network
Support through your entire compliance journey- from prep to assessment- with our network of CMMC consultants & auditors.
Learn More about PreVeil’s Solution
PreVeil Drive
Encrypt, store and share files containing CUI while using granular access to control permissions. Impervious to costly ransomware attacks. Integrates with Explorer, Mac Finder and on browsers.
PreVeil Email
Send and receive end-to-end encrypted messages using your existing email address. Protects against phishing scams and seamlessly integrates with Outlook, Gmail, and Apple Mail.
Work from Anywhere
PreVeil Email and Drive are also available as a free encrypted app on iOS and Android phones and tablets.
Share with 3rd Parties for Free
Subcontractors and other 3rd parties can create PreVeil accounts for free, so you don’t need to manage and pay for costly Guest Accounts.
Compliance Accelerator
Cut your CMMC documentation work by 60%, expedite compliance and save tens of thousands of dollars. Includes C3PAO-validated videos, pre-filled documentation (SSP, SOP, etc), & 1×1 support from our compliance experts if you get stuck.

Preferred Partner Network
Our preferred network of Assessors, Consultants, and Service Providers are vetted by our Compliance Team and offer a variety of services to help accelerate your compliance journey.
Proven Compliance at a Fraction of the Cost
Defense contractors & C3PAOs have used PreVeil to achieve CMMC compliance with perfect 110 scores

Construction Firm
“Cost was a big factor for why we chose PreVeil. We also loved the ease of implementation and how easy it was to teach a user how to use PreVeil“
Trusted by those who certify compliance. Used by those who must achieve it.