If you’re a government contractor, you’ve likely come across the term CUI Basic. But what is CUI Basic, really? And why does it matter for your organization?
In this comprehensive guide, we’ll break it all down: what qualifies as CUI Basic, how it differs from CUI Specified, real-world examples, compliance requirements, and why protecting this type of data is essential for national security and business continuity.

What is CUI Basic?
Controlled Unclassified Information (CUI) refers to sensitive but unclassified data that the federal government requires to be protected. It replaces older, inconsistent markings like “FOUO” (For Official Use Only) and “SBU” (Sensitive But Unclassified).
CUI is divided into two main categories: CUI Basic and CUI Specified.
CUI Basic includes information that:
- Is not classified,
- Requires safeguarding due to government policy,
- But is not subject to specific legal handling requirements.
Instead, protection requirements are standardized under 32 CFR Part 2002 and NIST SP 800-171.
CUI Specified, however, includes controlled unclassified information that must be protected in accordance with legal or regulatory mandates.
Example of CUI Basic
Imagine a defense subcontractor providing technical specs and engineering drawings for a naval drone. The data isn’t classified or subject to ITAR but still requires protection.
Since there are no special laws governing its handling—but it’s sensitive and tied to national security—it’s categorized as CUI Basic and must be protected under NIST SP 800-171.
Example of CUI Specified
An aerospace company working on a defense contract receives technical data related to missile guidance systems that falls under the International Traffic in Arms Regulations (ITAR). Because ITAR is a federal law that imposes strict controls on how such data is stored, accessed, and shared—especially with foreign nationals—this information is classified as CUI Specified. It requires not only the baseline protections of NIST SP 800-171 but also compliance with ITAR’s specific legal requirements, such as limiting access based on citizenship and using approved export-controlled systems.
CUI Basic vs. CUI Specified: What’s the Difference?
Understanding the difference between CUI Basic and CUI Specified is crucial for compliance and correct data handling. Essentially, CUI Basic is governed by general CUI program regulations, while CUI Specified is governed by specific laws and are subject to additional protections.
If there’s no law dictating extra requirements, the data is classified as CUI Basic.
Common Categories of CUI Basic
There are dozens of CUI Basic categories that span technical, financial, and legal areas. The NARA CUI Registry is the authoritative source for the full list.
Some Common CUI Basic Categories Include:
- Procurement and Acquisition Data
- Proprietary Business Information
- Legal and Contractual Information
- Infrastructure Protection Data
- Patent Applications
- Financial or Budget Information
- Privacy Act Data (when not elevated to Specified)
These types of information must be safeguarded even though they are unclassified.
Compliance Requirements for CUI Basic
Contractors handling CUI Basic must meet strict cybersecurity and compliance obligations. These include the following standards and frameworks:
NIST SP 800-171
This is the core standard for protecting CUI Basic. It includes 110 controls across 14 categories. Compliance involves implementing these NIST SP 800-171 controls, documenting them in a System Security Plan (SSP), and using a Plan of Actions and Milestones (POA&M) for any gaps.
CMMC Level 2
CMMC Level 2 directly maps to NIST 800-171 and applies to contractors handling CUI Basic. CMMC Level 2 assessments began in January 2025 and are expected to steadily increase as CMMC requirements are gradually incorporated into defense contracts over the coming years. During these assessments, organizations will be evaluated on their ability to meet all 110 security controls outlined in NIST SP 800-171, as well as how effectively they implement the procedures and policies detailed in their System Security Plan (SSP).
What is the Goal of Destroying CUI?
Knowing the difference between CUI Basic and CUI Specified is important, but so is the destruction of it. The goal of destroying CUI is to ensure that sensitive, unclassified government information cannot be accessed, reconstructed, or misused by unauthorized individuals once it is no longer needed.
Why CUI Destruction Matters
Just like classified information, CUI poses a risk if left unsecured—even after it’s outdated or no longer relevant. Improper disposal can lead to unauthorized disclosure of technical or procurement data, loss of competitive advantage or intellectual property, and national security threats through supply chain exposure.
Destroying CUI properly ensures that sensitive data doesn’t end up in the wrong hands, particularly in the context of cyber espionage, insider threats, or physical document theft.
Acceptable Methods for Destroying CUI
Per 32 CFR Part 2002, CUI must be destroyed in a manner that makes it unreadable, indecipherable, and irrecoverable. Acceptable methods include:
- For Paper: Cross-cut shredding, pulping, burning, or pulverizing
- For Electronic Media: Secure deletion, degaussing, cryptographic erase, or physical destruction (e.g., shredding drives)
Organizations must also follow any additional requirements set forth in their agency contracts or internal policies. Some types of CUI Specified may have their own mandated destruction protocols.
Why Protecting CUI Basic Is Critically Important
CUI Basic is a high-value target for cyber adversaries. Its protection is essential for national security, contract success, and business continuity.
National Security Implications
CUI Basic includes data on military systems and components, defense supply chains, and procurement and acquisition. If compromised, this data can directly harm U.S. national defense capabilities.
Supply Chain Risk
Adversaries often exploit small or mid-sized contractors to access the broader supply chain. Protecting CUI Basic helps close these gaps.
Legal and Business Consequences
Failure to protect CUI Basic can lead to:
- Breach of contract
- Contract revocation or suspension
- Disqualification from future DoD opportunities
- Costly audits and reputational damage
Who is Responsible for Applying CUI Markings?
Responsibility for applying CUI markings lies with the creator of the CUI—whether within the federal government or among contractors and subcontractors who create, receive, or manage CUI.
Role of Federal Agencies
Agencies that originate CUI are responsible for:
- Identifying what constitutes CUI under the NARA CUI Registry
- Marking documents and data correctly before dissemination
- Training employees and contractors on proper CUI handling
Agencies also designate CUI senior agency officials (SAOs) to oversee implementation and ensure compliance across departments.
Role of Contractors and Subcontractors
When contractors generate or receive CUI as part of a federal contract, they are required to:
- Mark any CUI they create or modify according to the source agency’s guidance
- Maintain those markings throughout the document’s lifecycle
- Ensure subcontractors and team members follow the same marking and safeguarding rules
Markings typically include:
- A header or footer with the word “CUI”
- Category markings (e.g., “CUI – Controlled Technical Information”)
- Limited dissemination controls if applicable
Here’s an example of how CUI will be marked on a contract.
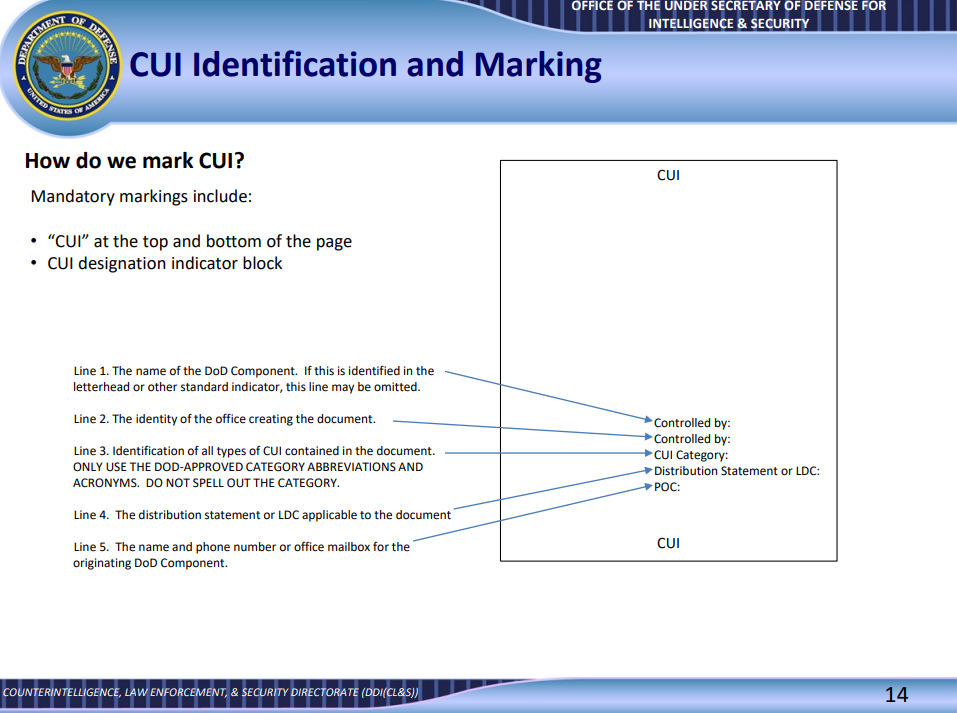
Tools and Guidance for Proper Marking
The National Archives and Records Administration (NARA) provides templates and guidance for marking CUI, along with training resources. Contractors should also refer to agency-specific requirements and contractual clauses.
How PreVeil Helps You Protect CUI Basic
PreVeil offers end-to-end encrypted email and file sharing designed to meet the requirements of NIST 800-171, CMMC Level 2, and DFARS 7012.
Why Organizations Choose PreVeil:
- End-to-end encryption for email and files
- Seamless integration with Outlook and Gmail
- Affordable for SMBs in the DIB
- Compliant with ITAR, DFARS, and CMMC
- Easy collaboration with primes, subs, and government partners
PreVeil helps defense contractors achieve and maintain compliance—without enterprise complexity or cost.
Get Started Today
PreVeil is trusted by thousands of contractors to protect CUI Basic and comply with NIST 800-171 and CMMC 2.0. We can help you simplify compliance, secure your data, and safeguard your contracts.