Today, many in the enterprise see O365’s email encryption for Outlook as the best-in-class security for messaging. Unfortunately, the reality is that Microsoft’s email encryption standard has serious deficiencies that leave messages unsecured and vulnerable to attack. While the platform provides numerous security options, these options are unable to meet today’s overwhelming security challenges.
This blog will look at the security challenges inherent in O365’s encrypted email options. Going from least secure to most, we will look at:
- Transport Layer Security (TLS)
- Office Message Encryption (OME)
- s/MIME
- Information Rights Management (IRM)
The Outlook on Microsoft email
TLS – The Standard Outlook on Protecting Data
Today, NIST standards recommend the use of Transport Layer Security (TLS) to protect messages in transit to and from the email server. By default, O365 ensures TLS for messages by ensuring messages go through an encrypted layer from the user’s inbox to the email server. The goal of TLS is to prevent an eavesdropper from snooping on messages or using a sniffer to intercept messages.
A significant problem with TLS though is that it does nothing to encrypt the text of the message itself. While the transport layer is encrypted, the message itself remains in plain text. Additionally, TLS does nothing to ensure encryption from the sender’s email server to the recipient’s email server. If the recipient’s server does not require TLS then the message will remain as an unencrypted email.
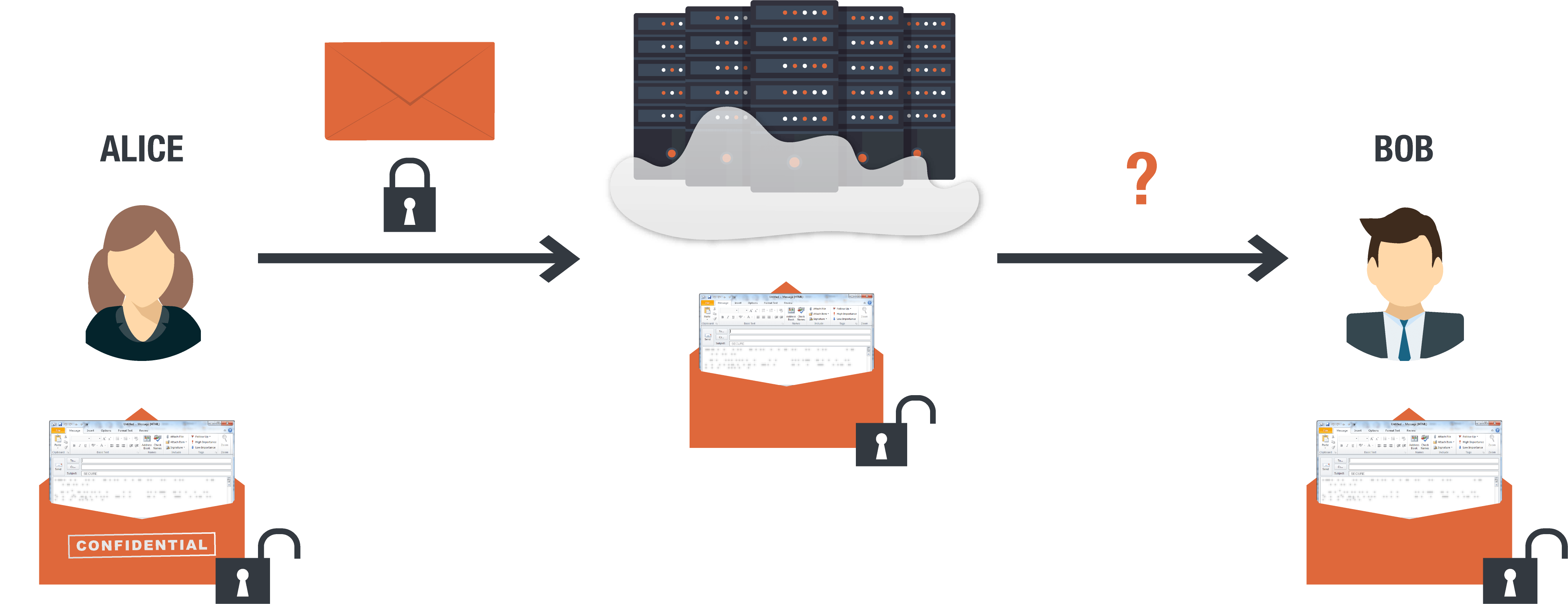
If the enterprise is relying on TLS then its email remains vulnerable . If an enterprise is solely relying on TLS, messages are not encrypted on the client nor on the email server but rather only in transit. Additionally, the email might not be encrypted as it travels to the recipient’s email server and their client. At each of these unencrypted points, the email is vulnerable to attack.
The Outlook on Office 365 Message Encryption (OME)
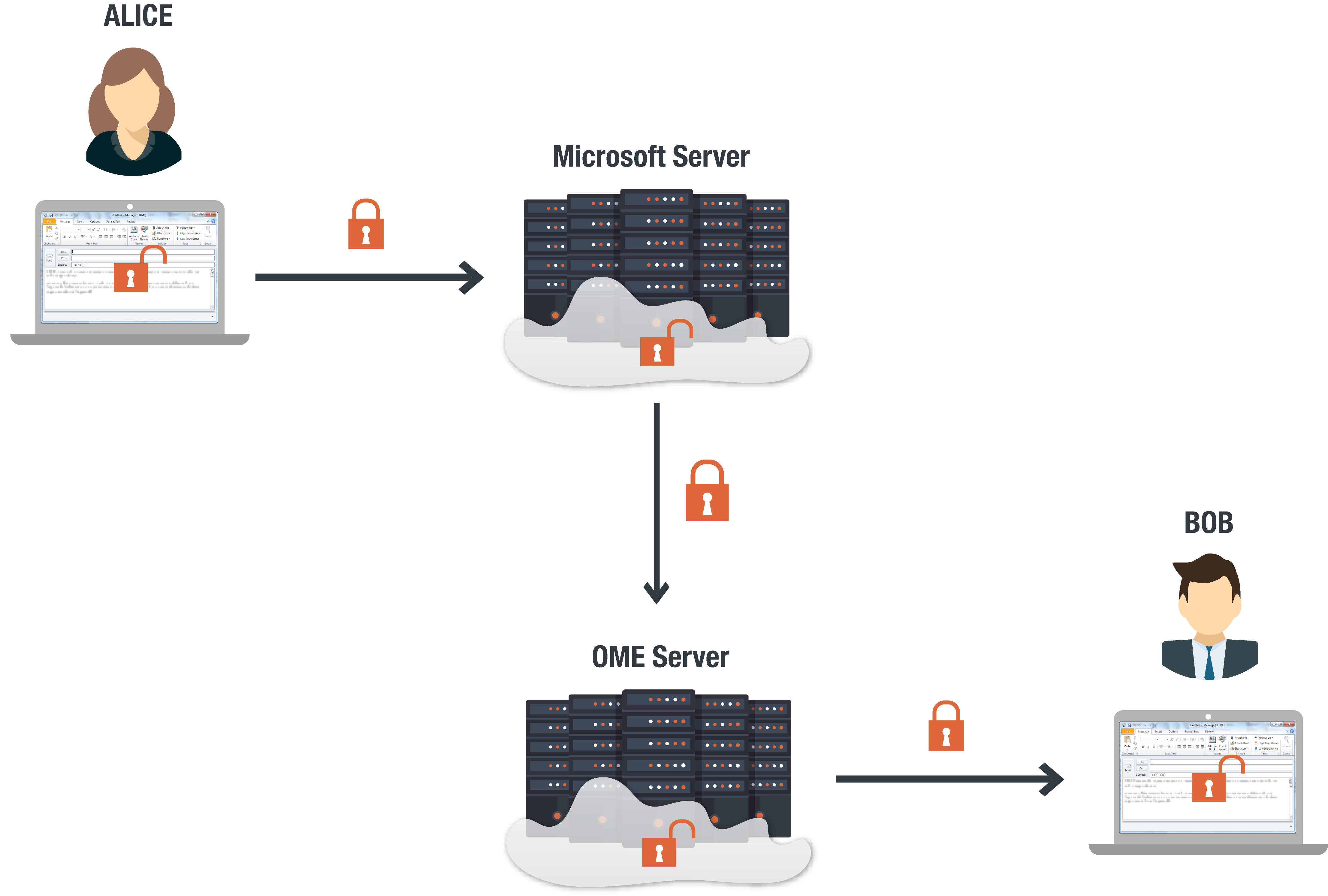
Microsoft also provides Office Message Encryption (OME) for encrypting email in Outlook. OME is a rules-based security tool where Microsoft manages and stores the encryption keys. OME secures messages with these encryption keys once they arrive to the OME server. Messages that meet specific conditions will then be encrypted.
Admins can set up transport rules that determine when encryption is used based on the content of the message. If a user sends a message that matches the encryption rule, encryption is applied automatically.
To set up OME rules for your enterprise, the IT admin needs to:
- In a web browser, sign in to Office 365.
- Choose the Admin tile.
- In the Office 365 admin center, choose Admin centers > Exchange.
- In the EAC, go to Mail flow > Rules and select New > Create a new rule
- In Name, type a name for the rule, such as Encrypt mail for Finance@MyCompany.com.
- In Apply this rule if select a condition, and enter a value if necessary. For example, to encrypt messages going to Finance@MyCompany.com:
- In Apply this rule if, select the recipient is.
- Select an existing name from the contact list or type a new email address in the check names box.
- To select an existing name, select it from the list and then click OK.
- To enter a new name, type an email address in the check names box and then select check names > OK.
- To add more conditions, choose More options and then choose add condition and select from the list.
If you want to apply the rule only if the recipient is outside your organization, select add condition and then select The recipient is external/internal > Outside the organization > OK.
- To enable encryption using the new OME capabilities, from Do the following, select Modify the message security and then choose Apply Office 365 Message Encryption and rights protection. Select a template from the list, choose Save, and then choose OK.
- The sender then composes a message in Outlook, selects Options> Permission, and selects the appropriate permission level and then sends the message.
The admin will need to repeat these steps for rule creation for every encryption rule they wish to enforce.
The challenge of implementing multiple encryption rules is only a part of the challenge of using OME. A bigger challenge is that OME servers can only enable the encryption rules once they have read the email and determined that encryption is required. While some users might not worry if Microsoft reads their emails, the reality is that this vulnerability creates a large hole in the enterprise’s security. If Microsoft can read your email than so can attackers.
In April 2016, Microsoft filed a suit against the U.S. government. Microsoft filed the suit because they required the company to hand over customer email and not inform the customers it had done so. Of course, the U.S. government was only able to make this request because Microsoft had the keys to the server in the first place.
In 2013, British journal The Guardian reported that Microsoft provides the NSA with access to messages sent through their Outlook.com prior to encryption. This step by Microsoft has helped the NSA get around the encryption Microsoft provides for its other services. Additionally, Microsoft’s privacy record has been rather spotty, particularly with ongoing controversy surrounding data collection in Windows 10.
How to encrypt email in Outlook using s/MIME
S/MIME is another email encryption standard Microsoft provides for encrypting email in Outlook. S/MIME is a certificate-based encryption solution that allows IT admins to provide end-to-end encryption for email. By definition, s/MIME ensures that only the sender and the intended recipient can open and read the message. A digital signature helps the recipient validate the identity of the sender. Below is a diagram for how s/MIME encryption works to send a message in Microsoft Outlook.
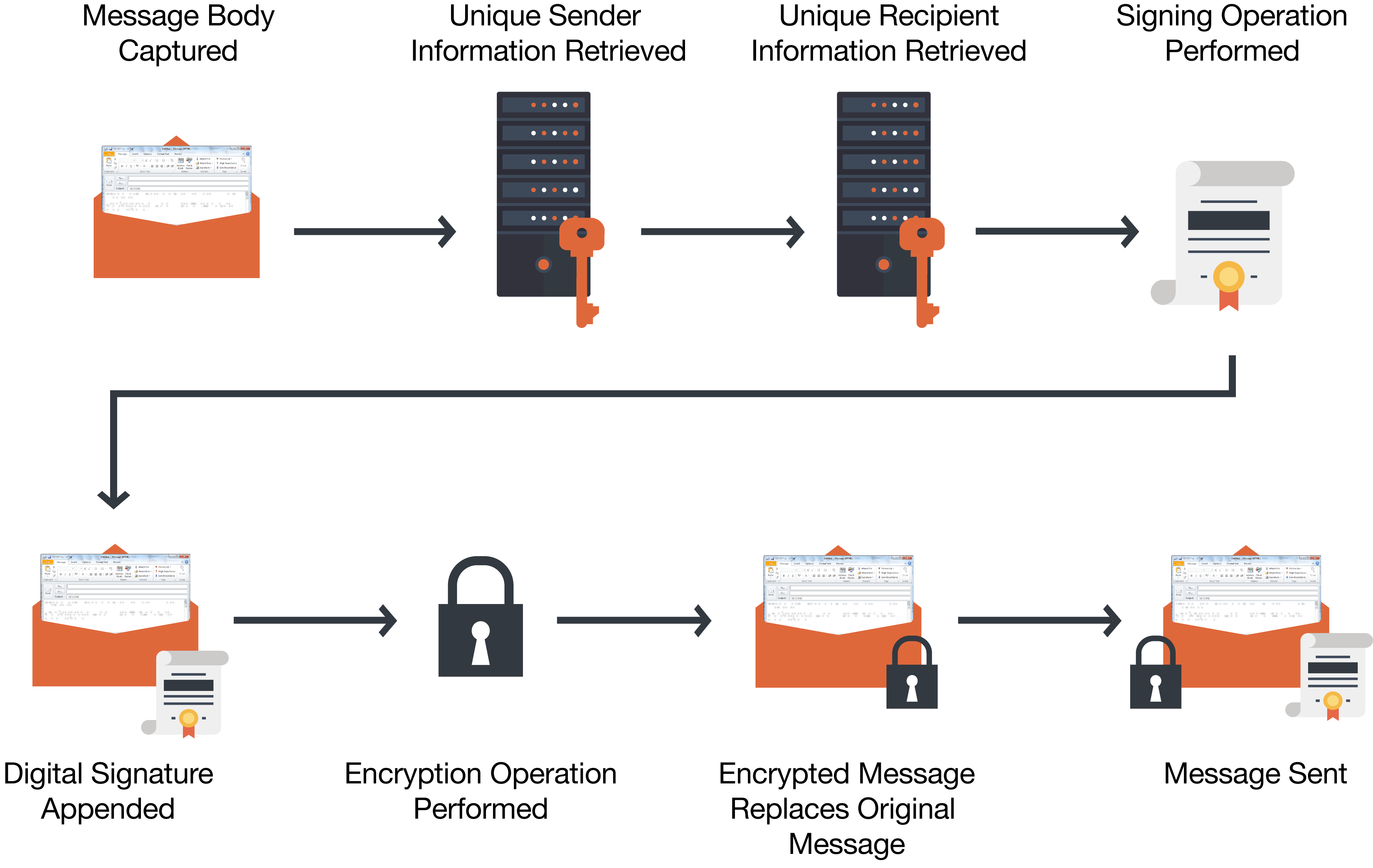
Here are the steps for how an IT admin should set up O365’s s/MIME:
- Install a Windows-based Certification Authority and set up a public key infrastructure to issue S/MIME certificates.
- Publish the user certificate in an on-premises Active Directory Domain Services (AD DS) account in the UserSMIMECertificate and/or UserCertificate attributes. Your AD DS needs to be located on computers at a physical location that you control and not at a remote facility or cloud-based service somewhere on the Internet.
- Set up a virtual certificate collection in order to validate S/MIME. This information is used by Outlook on the web when validating the signature of an email and ensuring that it was signed by a trusted certificate.
- Set up the Outlook or EAS end point to use S/MIME.
Because S/MIME receipt requests must include a digital signature, you must have a digital ID to request an S/MIME receipt.
- In an open message, click Options.
- In the More Options group, click the Message Options Dialog Box Launcher .
- Under Security, click Security Settings.
- Select the Add digital signature to this message check box.
- Select the Request S/MIME receipt for this message check box.
- Click OK and Close on the Security Properties and Properties dialog boxes.
- Send your message.
In addition to the multiple steps required for sending a message through s/MIME, the platform requires that both sender and recipient are using s/MIME. If the recipient is not using s/MIME then the pair cannot take advantage of the end-to-end encryption it provides.
Furthermore, s/MIME is vulnerable to attack. As was shown in last year’s eFail revelation, s/MIME is vulnerable to man-in-the-middle attacks. This vulnerability means that s/MIME lacks the ability to prevent would be attackers from taking advantage of the platform and reading users’ messages.
How to encrypt email in Outlook using Information Rights Management (IRM)
IRM is a Microsoft encryption standard that protects email and documents by preventing sensitive information from being printed, forwarded, or copied by unauthorized people. For example, a company administrator might create a template called “Confidential Financials”. “Confidential Financials” could specify that an e-mail message using that policy is only opened by users inside the company domain.
When a user sends an email that has the “Confidential Financials” rule in the email header, the standard is implemented. Alternatively, the user can manually enable the rule.
Steps to implement IRM
Implementing IRM begins with the admin creating rules to govern the behavior of the email.
- Sign in to Office 365 as a global admin or SharePoint admin.
- Select the app launcher icon in the upper-left and choose Admin to open the Office 365 admin center. (If you don’t see the Admin tile, you don’t have Office 365 administrator permissions in your organization.)
- In the left pane, choose Admin centers > SharePoint.
- In the left pane, choose settings.
- In the Information Rights Management (IRM) section, choose Use the IRM service specified in your configuration, and then choose Refresh IRM Settings. After you refresh IRM settings, people in your organization can begin using IRM in their SharePoint lists and document libraries.
How end-users can implement IRM:
- Create a new email in Outlook
- Click on the Options tab in the header
- Select the permissions for the email by clicking on the Permission block and choosing the appropriate standard
- Select More Options dialogue launcher to determine when the message will expire
- Send email
- Repeat these steps for every email that must be secured by this standard
IRM was designed to encrypt messages so they couldn’t be forwarded, printed or downloaded. However, these protections are easily bypassed by simply taking a screen shot of the text. Moreover, admins maintain the keys for IRM which means that they have the ability to decrypt the messages. If an admin is able to decrypt the message then so can an attacker.
How to seamlessly encrypt email in Outlook to ensure maximum security
There is a better solution to answer the question of how to encrypt email in Outlook. This solution starts with PreVeil’s easy to use email encryption platform protected with end-to-end encryption. With end-to-end encryption, the email is encrypted on the user’s device and is only ever decrypted on the user’s device. Unlike TLS, OME and IRM, PreVeil never decrypts messages along the way.
Unlike s/MIME, PreVeil also provides methods for key management so that the user is never challenged to access their data if they lose their device. PreVeil also offers auto-encrypt so that senders don’t need to remember to add labels to the email header.
Here’s how to encrypt email in Outlook once you have downloaded the PreVeil application for email:
- Go to https://www.preveil.com/download/ and download the version of PreVeil you wish to use. Choose between Windows, Mac, AppStore and Google Play
- On the next screen, click the “Download” button. Another screen displays to let you know that the PreVeil installer is downloading.
- When the download is complete, you can access the PreVeil.exe file in your Downloads folder
- Go to preveil.com/app to create your account. You are taken to your new PreVeil Inbox and provided with the opportunity to install PreVeil into Outlook.
- Click on <<Add PreVeil to Outlook>> in the interface
How to send an encrypted email in Outlook
- Go to Outlook and look for your Encrypted Inbox
- Click on <<New Email>>. Enter the recipient in the To field and compose your message
- Click on send
If your recipient has PreVeil installed on their end, they will be able to easily read the message either in the PreVeil application, Outlook, gMail or MacMail. Otherwise, they will receive a link in their email that allows them to either download the PreVeil application or read the encrypted in their browser.
CONCLUSION
PreVeil is able to overcome the challenges that Microsoft’s native email encryption platforms provide and enable users to encrypt email in Outlook.
With PreVeil, you can take control of the enterprise’s inbox and secure email from phishing and spoofing.
Want to learn more about how to encrypt email in Outlook? Contact us!